How do PGP keys work
- Tutorials
- by Jacob Riggs
- 06-05-2020
PGP (Pretty Good Privacy) encryption has become a long-standing pillar for protection and security for one primary reason: it permits you to send a coded message to somebody without sharing a key in advance.
Suppose you wanted to send a sensitive message to someone without anyone else being able to access the content. Perhaps the best arrangement would be to encrypt it to a symmetric key that only you and the recipient know. If an attacker intercepts your message, nothing can be deciphered. Systems like this work well, but there is one major flaw – how can you send an encrypted message to somebody without an already-established secure channel to share keys?
Public Key Cryptography
This is a problem that PGP solves with something referred to as public key cryptography, which permits the secure sharing of information irrespective of physical distance or boundaries and without the need for establishing secure prior contact.
Encryption / Decryption
In public key cryptography, encryption and decryption processes rely on a mathematically unique key pair. This consists of two keys, one termed a public key and the other a private key, both keys being capable of encrypting and decrypting one another. A public key represents a one-way function similar to that of an open padlock – a security property that any individual can easily lock, but only the private key holder can open. Crucial to the nature of this operation is that the private key to decrypt a public key encrypted message must always remain secret, known only to the key pair owner.
The image below illustrates an example of the encryption and decryption process.
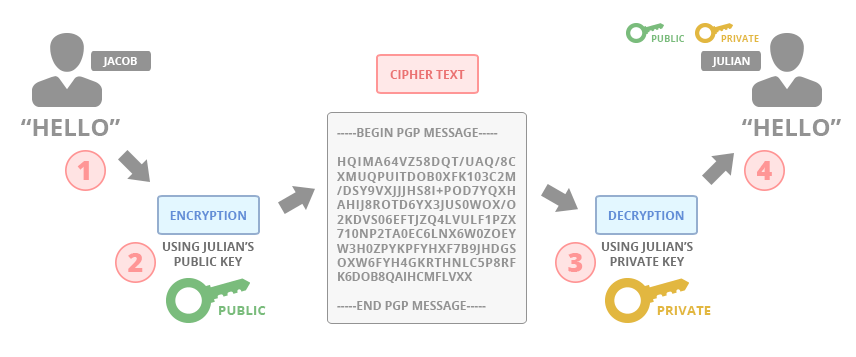
If Jacob wants to send Julian an encrypted message, he requires Julian’s public key. This means Julian must share his public key with Jacob. Jacob can then take Julian’s public key, use it to encrypt a message, and send the encrypted cipher text to Julian. Upon receipt, Julian can then use his private key to decrypt the message.
Fingerprinting
One issue with public keys is impersonation. There is no easy way to guarantee that a particular public key published online actually belongs to a specific individual. This means an attacker could generate their own key pair and publish their own public key impersonating a specific target.
To get around this, PGP users tend to publish fingerprints of their public keys on multiple platforms. This usually includes social media and key directories, but can also include other media such as email signatures and business cards. Fingerprints can be thought of like a barcode – a unique identifier for a specific property. Fingerprints are the result of a mathematical one-way function termed hashing, which converts the public key block property into an input value, then compresses it into a fixed length numerical string output. This is conveniently easier to read and appropriately referred to in cryptography as a digest.
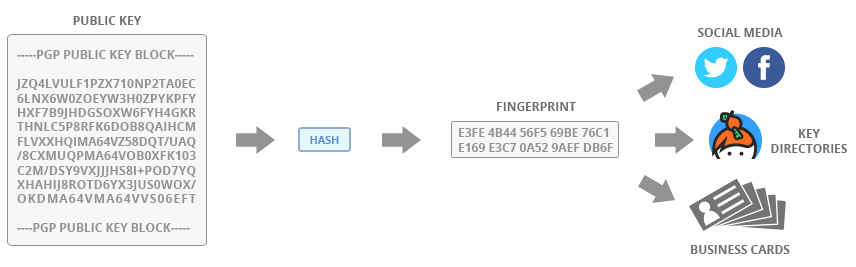
Publishing a fingerprint through multiple channels increases an impersonation attack cost, as for an attacker to effectively impersonate a PGP user in practice, they would need to compromise every platform the legitimate fingerprint was published on. This also makes impersonation attacks easier to identify in practice.
Message Signing
Another core component of PGP is message signing. This is the process of signing a message with a unique digital signature.
The image below illustrates an example of the signing process.
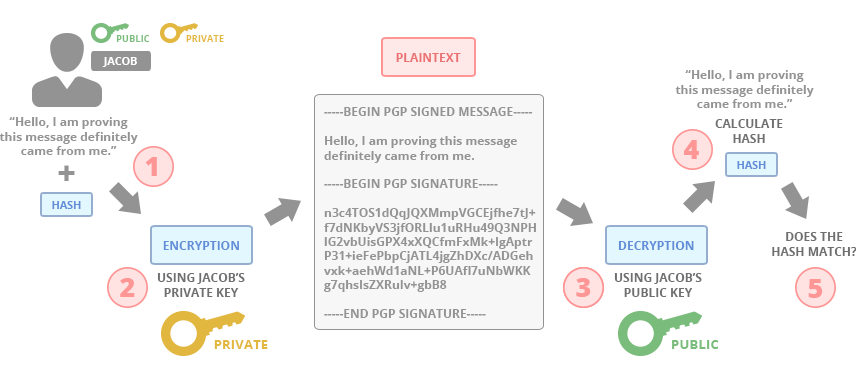
If Jacob wants to send a signed message to prove it came from him and has not been modified in transit, he hashes it first, then encrypts it using his own private key. If a recipient can decrypt the message using Jacob’s public key, they know that it must have been encrypted using Jacob’s private key, which only Jacob has access to, and can therefore conclude that the message must have originated from Jacob. By hashing the message again and comparing it to the expected hash value, a recipient can also conclude whether or not the message has been modified in any way during transit.
Combining signing with encryption provides the following assurances:
- Confidentiality – the guarantee that no party other than the intended recipient can access the message content.
- Integrity – the guarantee that the message was not modified in transit.
- Authentication – the guarantee that the identity of the sender can be verified.
- Non repudiation – the guarantee that the sender cannot reasonably deny having sent it.
In my next blog post I'll cover the key pair generation process and provide guidance on how to set up and manage your own PGP keychain.
ABOUT THE AUTHOR
