Write-up of a simple Activision security vulnerability
- Write Ups
- by Jacob Riggs
- 22-10-2023
This will be a short write-up as this one took no more than two minutes to identify from start to finish, and I actually found it laying in bed half asleep on my phone. Be warned, it's so simple it's underwhelming. The vulnerability is not device specific so this write-up will use desktop device screenshots for ease of reference.
My friend forwarded me an InfoSec related job advert for Activision via LinkedIn on the weekend.
I took a quick look as I’m a long-standing Activision customer, but the role wasn’t a fit for me. However, reading through the job description I noticed the benefits at the bottom of the page and was curious what entitlements Activision employees enjoy.
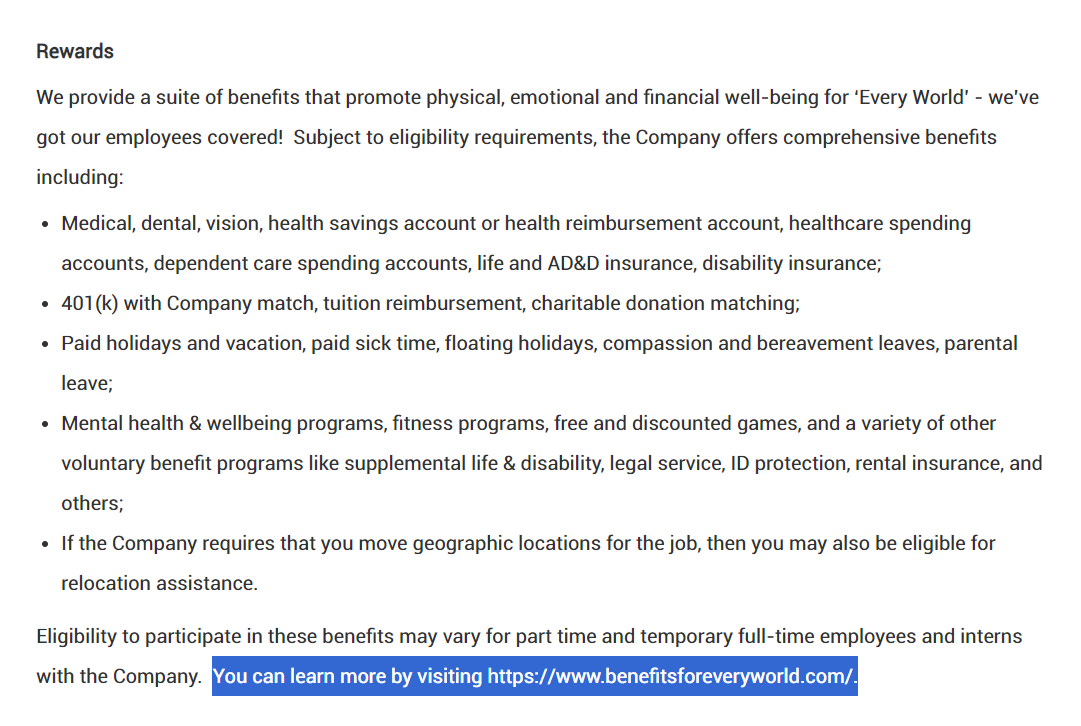
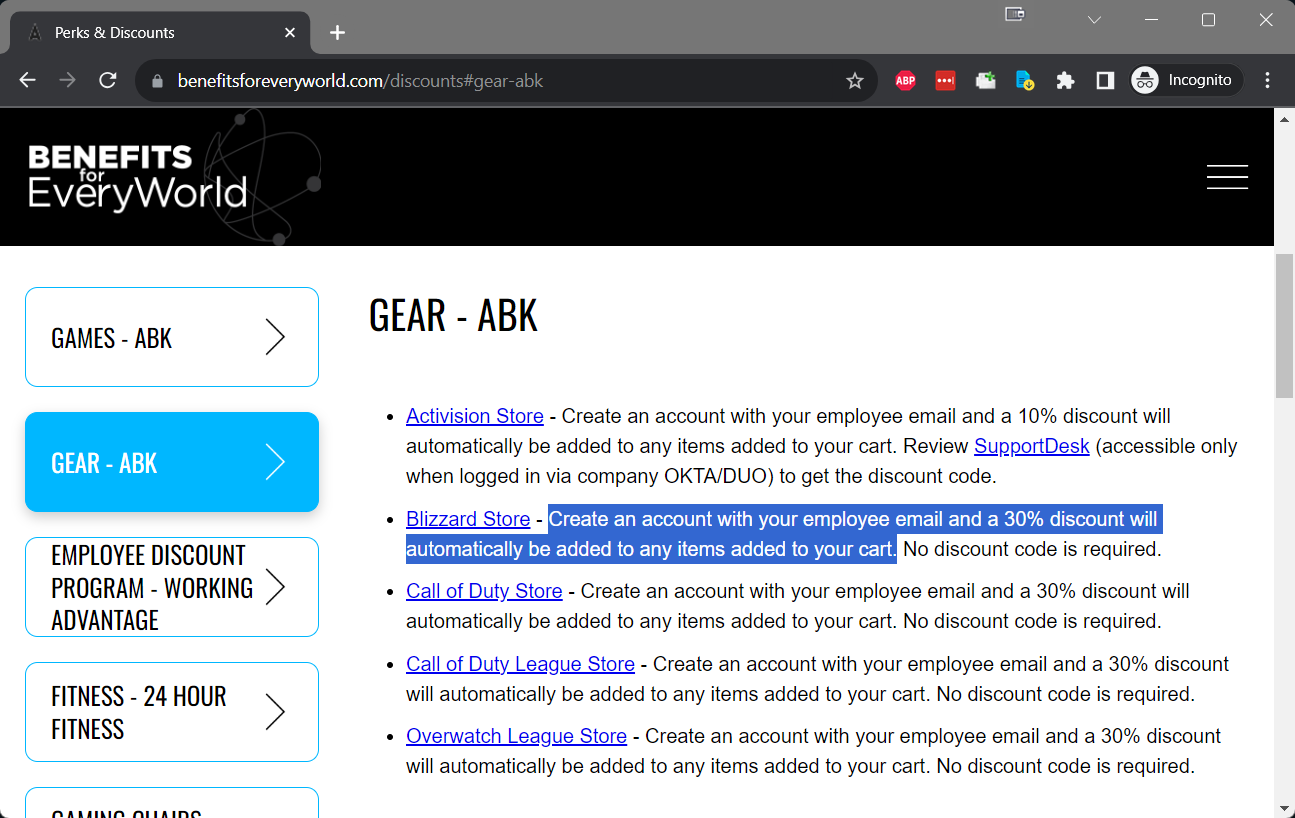
I took note of what appeared to be a custom employee benefits portal. As bug hunters know all too well, 'custom' often = vulnerabilities. I could see employees enjoyed a 30% discount from a number of stores when registering with their employee email address.
I quickly registered to see what the standard account creation and email activation process looked like...

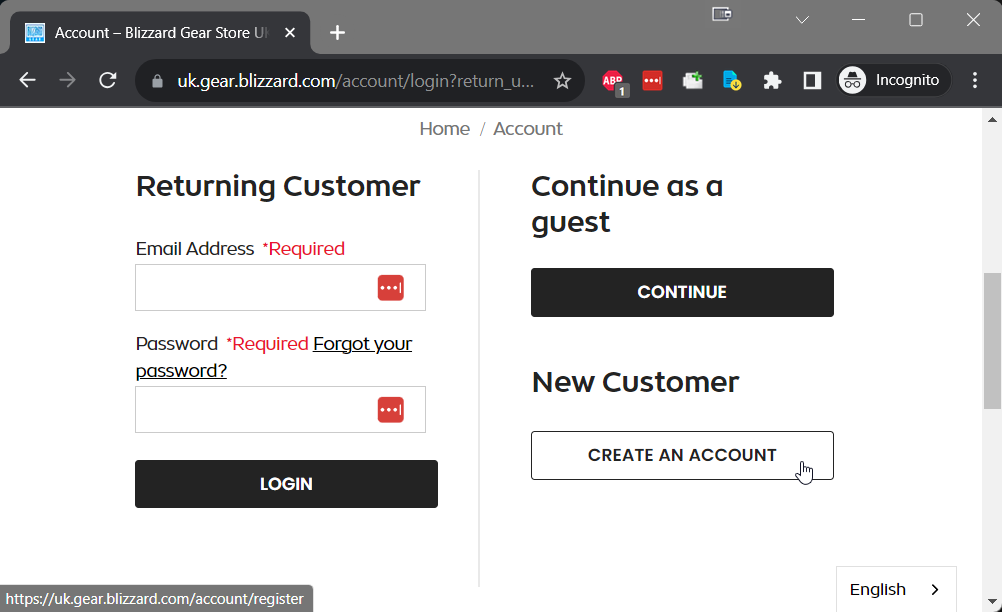
I proceeded to input my personal email address and following registration form submission, I immediately received an automatic account activation email.

My account was automatically activated? No double-opt in? Interesting! You can probably guess what I tried next...
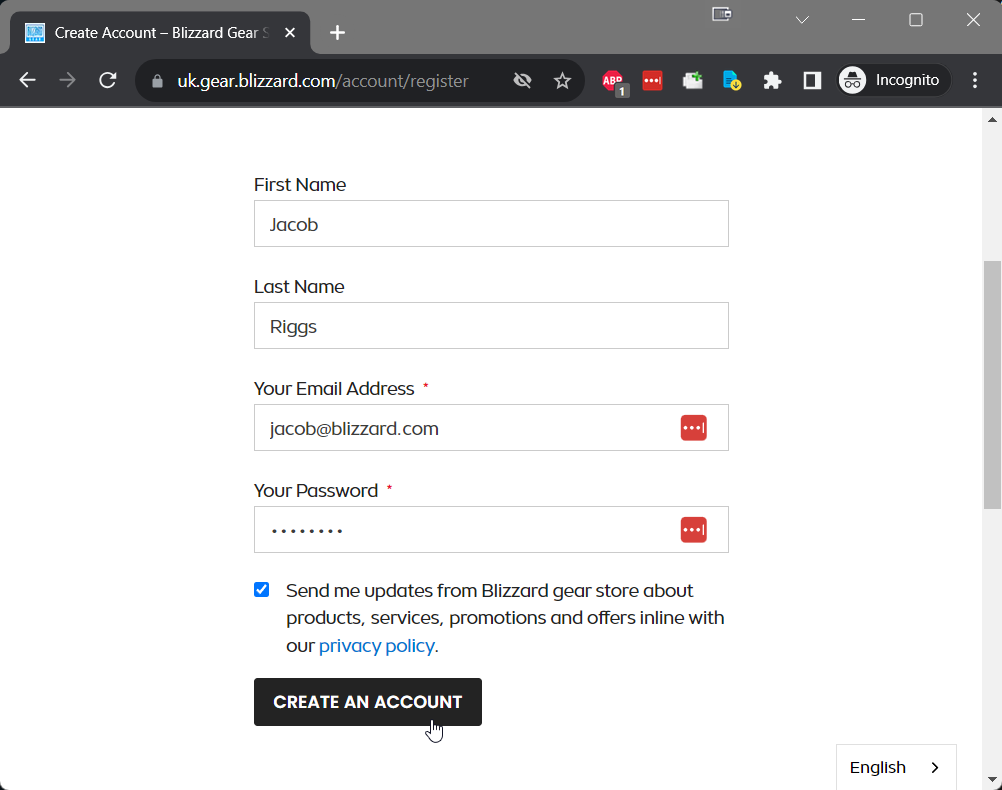
Success! I managed to register and auto-activate registration for what the application might recognise as an employee account. Now to see if the 30% discount applies when adding items to cart.
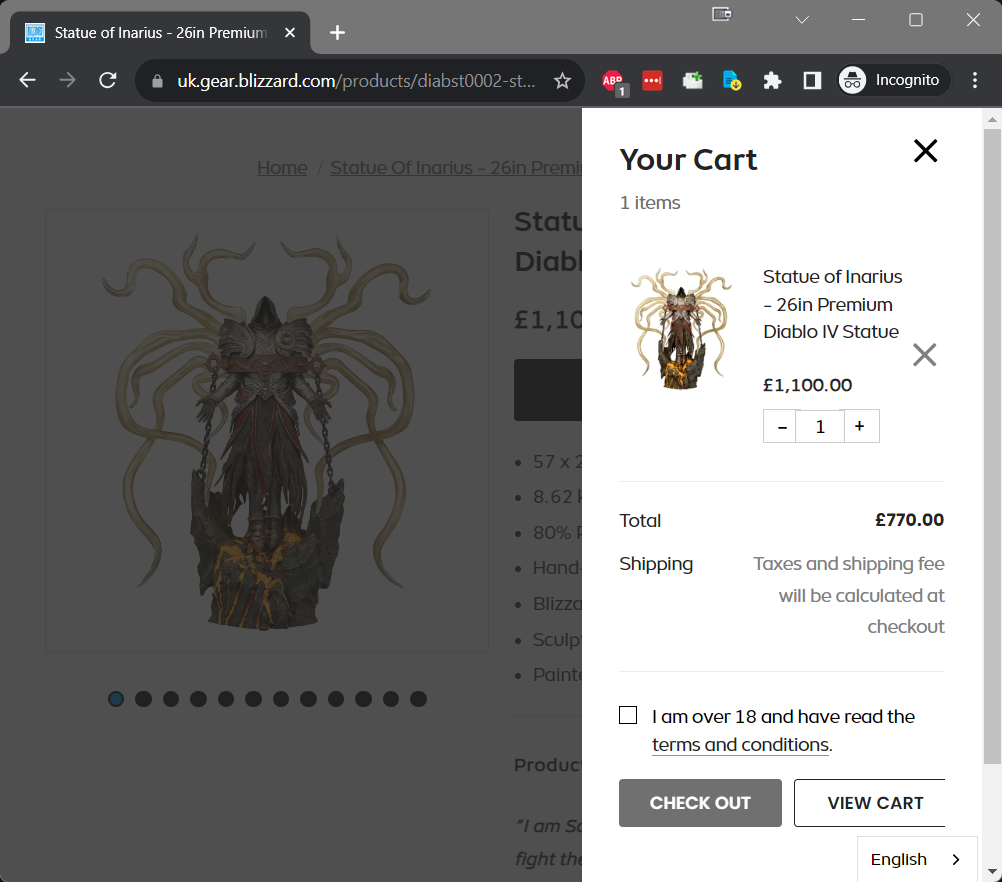
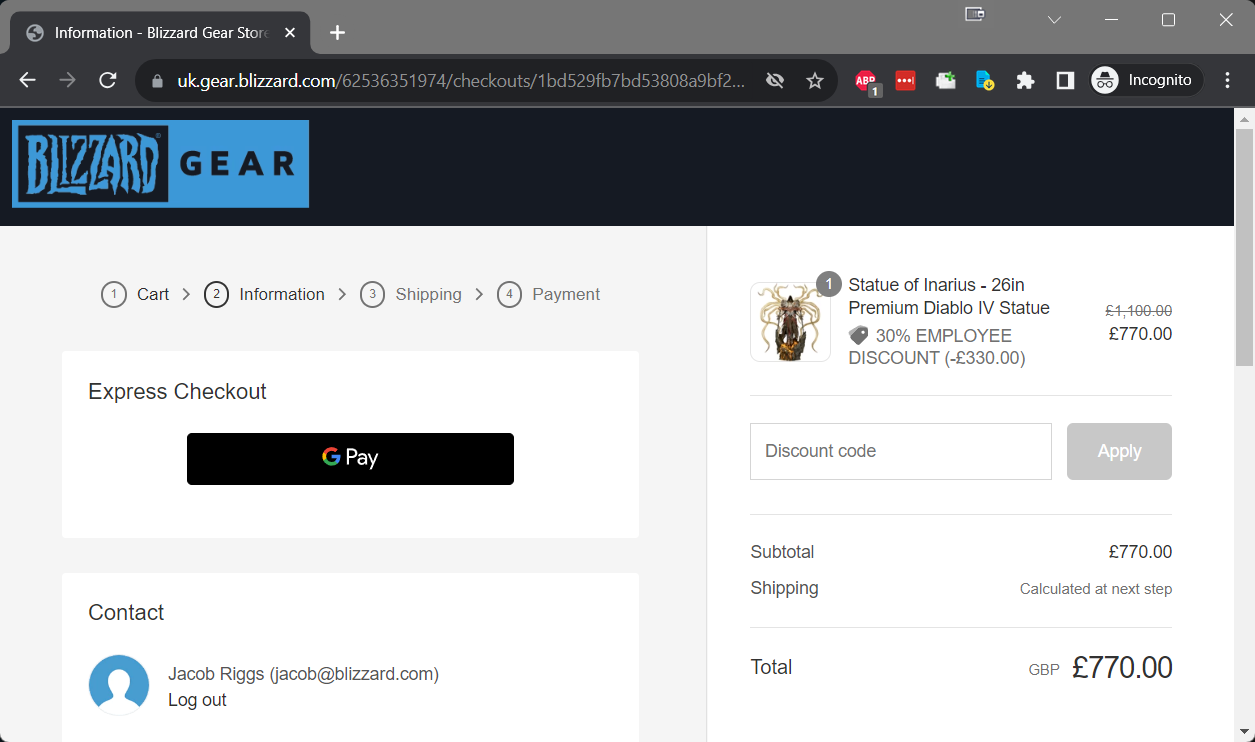
Seems promising. Now to see if I can reach the checkout page without any validation requirements.
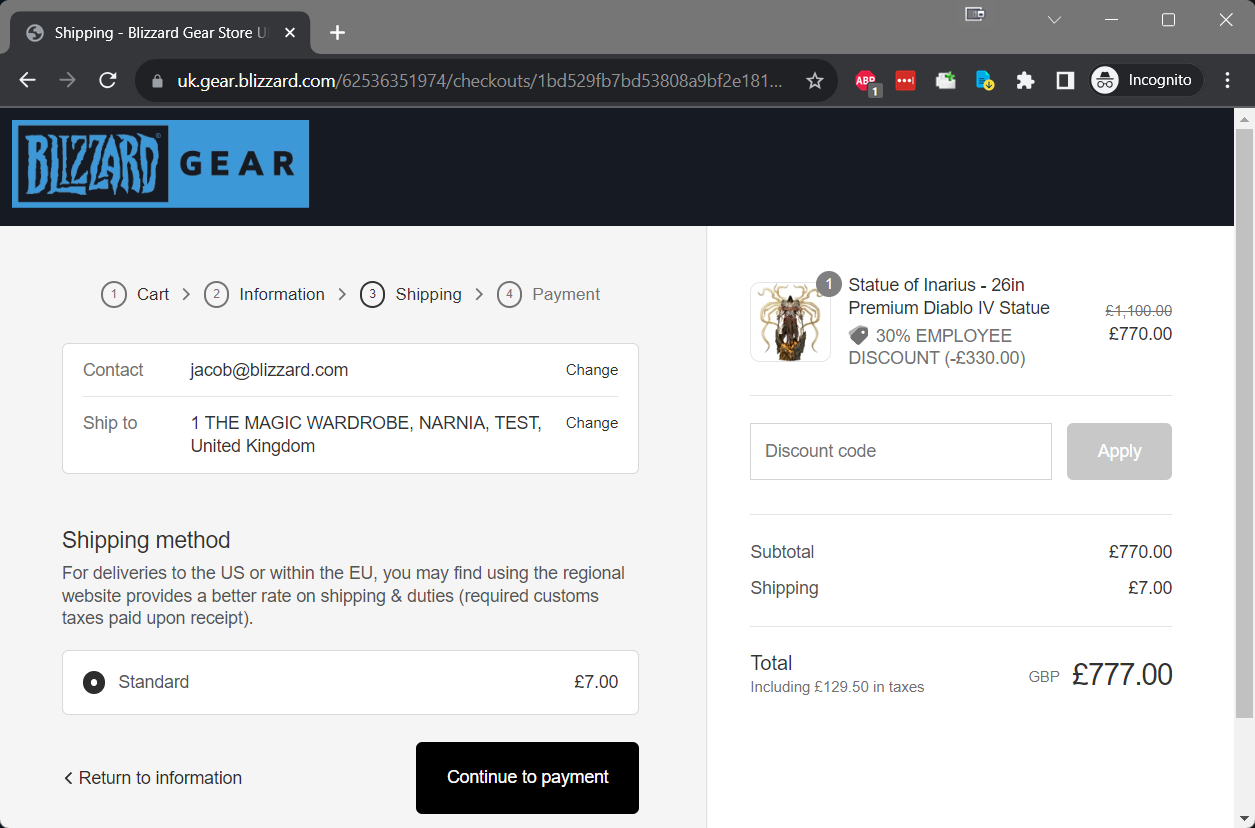
Success! From here the payment process gets handed over to the Shopify API for completion. I of course made sure to not proceed further and began writing up my findings for responsible disclosure. In determining the potential scope of impact I was able to see that the following stores were affected by this vulnerability:
My report was provided sameday, in-gratis, and in good faith. Given the size of Activision's customer base, the low complexity required to exploit this particular vulnerability, and the financial impact it could have, it's of course possible I wasn't the first to find this. For this reason I also encouraged Activision to consider investigating if any abuse may have ocurred prior to my report.
Repeat efforts were made over the span of 109 days to serve Activision notice of this vulnerability and encourage remediation prior to public disclosure. At the time of this write-up publication no official response had been received.
ABOUT THE AUTHOR
