How to validate file integrity with checksums
- Tutorials
- by Jacob Riggs
- 10-05-2020
A checksum is a unique string derived from a block of digital data for the purpose of detecting any changes which may have been introduced during its transmission or storage. In short, checksums are a file integrity validation measure. If you download a file from an untrusted source, a checksum can help you validate that the file you have downloaded perfectly matches that which the file issuer intended. In practice, this helps identify any files which have been corrupted or maliciously altered in transit.
Checksums are commonly seen on websites alongside downloadable software binaries, patches, hotfixes, and updates.
Due to their low computational overhead, they are also useful in security operations for fingerprinting malware and can be added to anti-virus signature databases or stored as artifacts for future reference.
Windows:
HashTab is a free shell extension for Windows which integrates itself within Windows Explorer as a property page for files with a context menu to generate and compare hashes. Once installed, HashTab can be accessed by right-clicking a target file and navigating to Properties and selecting the File Hashes tab.
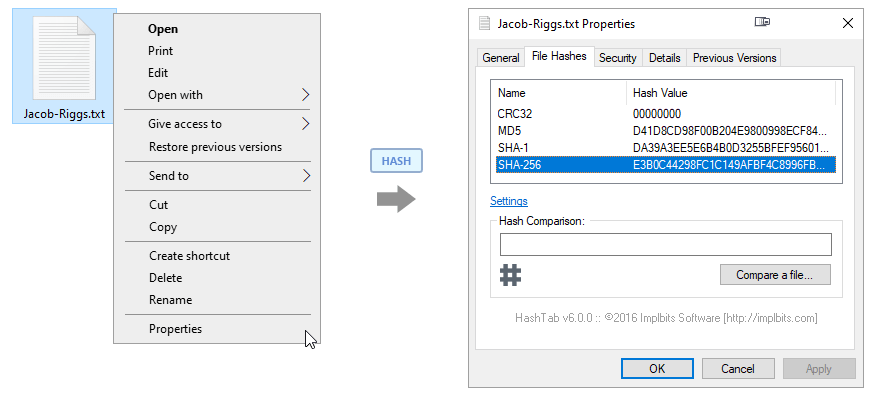
HashTab will then automatically attempt to hash the target file and report the relevant values.
Alternatively, Windows comes with a pre-installed utility called CertUtil, which can be used to generate hashes.
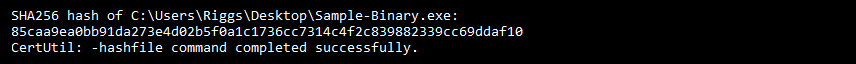
To generate a hash for a particular file using CertUtil, open CMD (Command Prompt) and type the following:
CertUtil -hashfile [TARGET FILE LOCATION] [DESIRED HASH ALGORTHM]
For example:

This will generate a SHA256 hash string which can then be compared against the checksum provided by the file issuer to verify the file integrity.
Linux:
Linux comes with a number of pre-installed checksum utilities. To generate a hash for a particular file using these, open terminal and type the following:
[DESIRED HASH ALGORITHM]sum [TARGET FILE LOCATION]
For example:
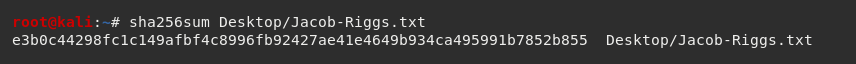
This will generate a SHA256 hash string which can then be compared against the checksum provided by the file issuer to verify the file integrity.

