How to perform SQL injection attacks
- Tutorials
- by Jacob Riggs
- 09-02-2020
SQL injections are one of the most popular server-side injection attacks. During an SQL injection attack, the attacker injects a malicious SQL query input. If the web application fails to sanitise that input, the query will be successfully executed on the server database and trigger an output response. These responses can vary, but most consist of error syntax leading to information leakage. Once an attacker possesses enough knowledge about the backend database table structure, they can inject specific commands to insert, update, and delete data within the database. If elements of an application communicate with a SQL database for authentication (such as login forms), a malicious query can also be leveraged to subvert the application logic.
How SQL injection attacks work
To explain how SQL injections work, I will use an example of a web application configured to require a username and password for authentication. This is typical of most web applications that have an SQL database on the backend.
When a username and password is submitted via this login form, the web application takes this user input and queries the backend database to see if those credentials exist. The SQL query this user input generates will look something like this:

This query commands the database to select any number of rows that match our conditions from users (where users is the table name), and then check the username and password columns for the user supplied input values. If the user supplied input values match those within the database, the SQL statement will be TRUE and the user will be logged in successfully. If any user supplied input values are incorrect, missing, or invalid, the SQL statement will be FALSE and the login will fail.
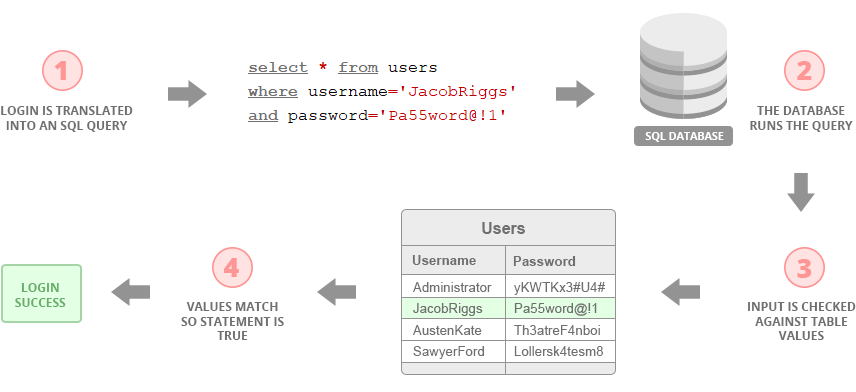
It is important to remember that the SQL query is always generated by the web application and that the only control the user ever has (in this example) is over the username and password input values within it. This means an attacker is limited to what those fields accept when crafting a malicious string in effort to manipulate an SQL query.
In this example, the objective of the attacker is to login successfully without knowing the user credentials. This means the focus of the attack will be to trick the SQL database into issuing a TRUE response to an attacker crafted query when attempting to login.
OR logic gates
To achieve this, an attacker can rely on an OR logic gate. An OR logic is a basic function that takes certain inputs and produces an output. The way this works can be illustrated via the simple A/B table below. This table shows that when rows A and B meet certain boolean conditions, the logic gate will produce a specific output.
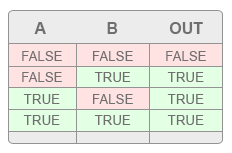 What is shown in this example is that the output TRUE is always consistent with TRUE inputs in any given row. This is irrespective of whether or not inputs within those rows also reflect FALSE. Putting it simply, the function of this logic gate defines any TRUE input as an overriding value which results in a TRUE output.
What is shown in this example is that the output TRUE is always consistent with TRUE inputs in any given row. This is irrespective of whether or not inputs within those rows also reflect FALSE. Putting it simply, the function of this logic gate defines any TRUE input as an overriding value which results in a TRUE output.
Example
To illustrate how this works in practice, I will be using the logic of this OR function in my SQL injection attack by amending the username value to the following:
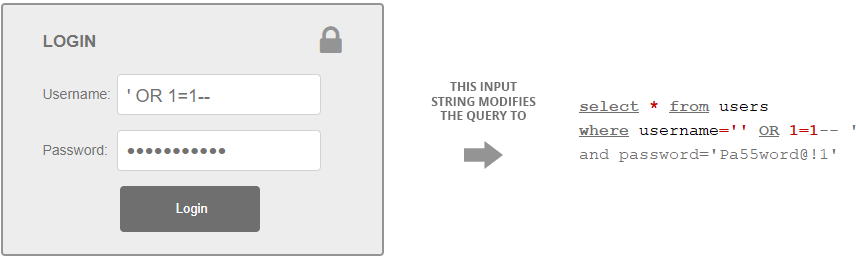
This query will return TRUE. The reason for this is because the first apostrophe closes the string parameter, and then the database takes the OR function and applies the 1=1 statement. As 1 is equal to 1, the database considers this part of the SQL statement TRUE. The purpose of the double hyphens is to comment out the rest of the SQL query, resulting in the database believing the conditions of the login are TRUE. This will result in the login being successful.
Whilst this example demonstrates a single SQL injection string, it is important to remember that there is no universal string an attacker can leverage to craft a working malicious query. SQL databases typically differ greatly in format, size, and content, as do the defensive measures some web applications adopt to validate user input. The conditions that need to be satisfied for an SQL injection to be successful will depend entirely on how any target web application is built.
Different SQL injection attack types
There are two primary types of SQL injection attacks, error based and blind based. Error based attacks rely on inferences an attacker can make from specific errors produced by a web server whenever specific SQL statements are submitted to it. Blind based attacks are a form of indiscriminate fuzzing, where the expected application output is usually unknown. Responses (or lack thereof) produced by a web server to blind based attacks can enable an attacker to make informed determinations about the database structure, which – when combined with a carefully crafted SQL query, can amount to exploitation.
Prevention
To prevent SQL injection attacks, the following layers of defence can be adopted:
- Special characters submitted as input such as ' and '' should be encoded before the web application passes them into an SQL query and special string characters used within input parameters should be escaped.
- Suspicious user inputs submitted should be checked against a predefined blacklist of strings and rejected wherever the same values are shared.

