How to avoid detection during a pen test
- Tutorials
- by Jacob Riggs
- 08-07-2020
Understanding how to cover your tracks during a pen test is important. The MITRE ATT&CK matrix defines this as defensive evasion, which consists of methods and techniques that an attacker may use to help avoid detection through network monitoring. Below are some defensive evasion techniques that can be used in practice during a pen test engagement.
Clearing Command History (ID: T1146)
Both Linux and Mac operating systems keep track of the commands users type in the terminal. The BASH shell will record keystrokes in the $home/ .bash_history file. During a pentest, once you obtain access to a Unix/Linux/Mac operating system, it is usually best practice to unset the history file to prevent the user/administrator from knowing what commands you were executing, as well as not commingling your dirty/malicious commands with a user's history. Unsetting the history file is as easy as shown here:
unset HISTFILE - The temporary history will not be written to disk.
export HISTFILE=0 - The temporary history will not be written to disk.
history -c - This will clear the temporary history file.
set +o history - Prevents commands from recording to the temporary history.
Administrators can counter the defense evasion attack by setting the variable read-only to help preserve the contents of the history file for forensic purposes.
Timestomping (ID: T1099)
A technique used to modify the timestamps of a file (the modify, access, create, and change times) is called timestomping. This technique can be executed by an attacker against files/directories that were modified. The timestomp feature in a meterpreter shell can be a good way to limit the digital footprint of reading/writing data on the file system. To see a list of options, you can use the following syntax:
timestomp -v - Display the UTC MACE values of the file.
timestomp -m - Set the last written time of the file.
timestomp -a - Set the last accessed time of the file.
timestomp -c - Set the creation time of the file.
You can see what the date timestamps look like before and after, then change it back to the before look. Imagine you wanted to change the contents of a user's logon script or even a scheduled task that points to a PowerShell file in the administrator's home directory called riggs-script.ps1 and add some arbitrary code to the file to assist with persistence. Once you modify the file, you can use timestomp to change the file back to the original values. This way your modification doesn't set off any red flags when looking at the date timestamp.
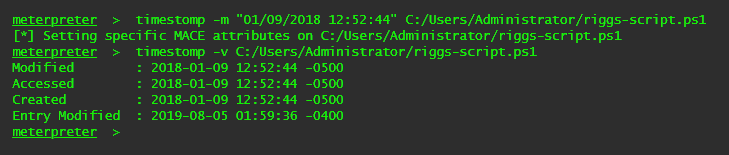
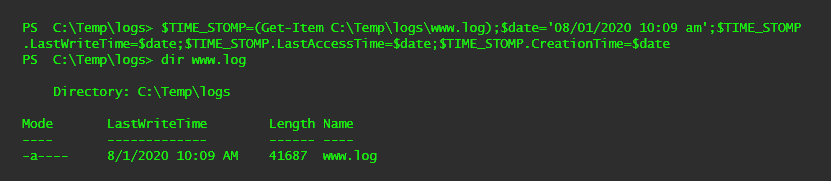
Let's say you are on a Windows database server after successfully exploiting an SQL injection vulnerability through the customer's web server. You want to remove your nefarious actions from the www.log and db.log files and timestomp them to a period of time prior to the attack.
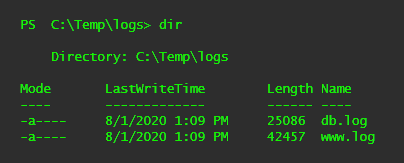
After you remove your malicious entries in the log, you can use PowerShell to change the file properties LastWriteTime, LastAccessTime, and CreationTime for each log file. To do this, you could use the Get-Item cmdlet to identify the item (file) you want to modify, define the date you want to set the files to (the format is MM/DD/YYYY HH:MM am/pm), and apply the new timestamp to each file property. This can help conceal your entry and allow you to continue with your testing objectives and not draw as much attention to yourself.
File Deletion (ID: T1107)
Malware, tools, or other non-native files dropped or created on a system may hadd to the attacker's digital footprint. Metasploit is a great way of avoiding this hurdle when exploiting and executing code from within the framework, as there are automated mechanisms for cleaning up tools and anything residing in memory. The attacker may also clean the contents from /var/log/* on Linux/Unix/Mac operating systems, or wipe out the Event Viewer database on Microsoft systems. To mitigate, organisations can leverage logging servers (e.g, SYSLOG) to send security-relevant messages and information to a central host. This will help make the attacker's job harder when covering their tracks if the log events are stored on another system or part of the network that they don't have access to.

