DDoS attacks and how to mitigate them
- General
- by Jacob Riggs
- 01-07-2020
In this era, cyber-attacks are gaining in popularity with more sophisticated techniques and attack deployment strategies being seen in the wild than ever before. DDoS (Distributed Denial of Service) attacks have gained popularity over the years, and as network systems advanced these types of attacks grew to become more refined. Many types of DDoS attacks now exist including HTTP flood attacks, SYN flood attacks, volumetric attacks, DNS amplification attacks, UDP flooding, ICMP flood attacks, and many others. In this blog post, I will walkthrough the basic and advanced concepts of a DDoS attack, what they are, the different types, and how companies can mitigate DDoS attacks with preventive techniques or measures to mitigate their effects.
What are DDoS attacks?
DDoS attacks or Denial of Service attacks are a malicious attempt to disrupt services offered by a server. In a typical DDoS attack, the intent of the attacker is to disrupt normal traffic of the target by maliciously overwhelming it with a coordinated flood of traffic, consequently denying any legitimate traffic access to the service. This attack is possible by bridging various types of computers and devices into a centrally controlled botnet and collectively pointing them all towards a target endpoint.
As multiple systems are required to carry out a DDoS attack successfully, IoT devices are the low-hanging fruit for attackers aiming to grow their own botnet. This is because the nature of the IoT market means manufacturing processes are often rushed and security controls are considered secondary. As a result, many IoT devices are released with high severity vulnerabilities which are trivial for opportunistic hackers to exploit.
Types of DDoS attacks
There are many ways to disrupt or suspend a server’s resources or computing operations, and hackers have found various ways to overwhelm servers using various simple techniques. Approaches like using botnets and automation to issue requests demand the targeted servers employ more computational power to handle them. Thus, most of the time, such attacks are successful. DDoS attacks can be broadly divided into three types, which reside within specific layers of the OSI model.
The first type are volumetric attacks. In this type, the attacker intends to saturate bandwidth of the target server and measures the intensity in bits per second. These include spoofed packet floods, ICMP floods, and UDP floods.
The second type of attacks are protocol attacks, which are together termed Layer 3 and Layer 4 attacks. These are initiated by targeting vulnerabilities in the network and transport layers of the OSI model. In this type, the main intention is to consume computational resources and can impact the infrastructure used to manage network traffic, such as firewalls and load balancers.
The third type are known as application layer Attacks. These include flooding GET / POST requests for images, files, or other large file size assets. These attacks are intended to crash the server and the intensity is measured in requests per second (rp/s). A higher rp/s rate leads to a faster server crash.
Layer 3 (L3) attacks
This type of attack takes advantage of flaws within the network layer protocols of the OSI model, and commonly include:
- Ping flood attacks – in this type of attack, the attacker attempts to crash the server by flooding it with ping requests until the server crashes.
- Smurf DDoS attack – early implementations of ICMP inherently had poor validation measures which made it easy for an attacker to spoof an IP address in an ICMP request. When using this in the context of a DDoS attack, the attacker sends a series of ping requests to thousands of servers. Once the requests are sent, the attacker then spoofs the target IP address and directs the response to the target system rather than their own IP address. However, this is now an uncommon attack vector as modern infrastructure is rarely vulnerable to this type of attack.
- ICMP ping of death attack – in this type of attack, the attacker deliberately sends ping requests with IP packets that are greater in size than the maximum allowed by the IP protocol. The network infrastructure, in accordance with TCP/IP, then divides the whole request into chunks that are processed and sent in request fragments. However, when all these fragments are combined together at the target server for processing, the server is unable to handle the computational demand and crashes. For this reason, many modern servers block ICMP requests altogether to prevent any variations of this attack getting through.
Layer 4 (L4) attacks
In this type, the objective is to increase the number of packets sent in under a second to the point that the server crashes. The impact is measured by packet per second (pp/s). In this type of attack, a service running on the server is usually targeted rather than the server itself.
- SYN DoS/DDoS attack – in this attack, the attackers exploit the ‘three-way hand shake’. This is done by exhausting the target’s resources by waiting through the TCP Timeout period one after another. In this way, the TCP handshake is never completed and the buffer is full of other waiting TCP handshake requests coming from legitimate sources. Eventually, the server crashes due to timeout requests and an overwhelming amount of resource consumption.
- SYN-ACK flood attack – In this attack, the attacker attempts to occupy all the space in a target server state space by sending SYN requests from spoofed IP addresses. Once the state space of the target server is full, it has insufficient free space to handle legitimate requests.
Layer 7 (L7) attacks
These attacks are prevalent on the application layer of the OSI model, and commonly include:
- HTTP Flood attack – in this attack, the upper layer of the of the target application is overwhelmed with HTTP requests. The attacker exhausts the server’s resources by saturating it with GET and POST requests for images, files, or some other asset from a targeted server.
- DNS amplification attack – in this attack, the goal is to flood a target with fake DNS lookup requests from open DNS servers that consume network bandwidth to the point that the site fails.
- WordPress DoS/DDoS attack – in this attack, the concept of XML-RPC (Remote Procedure Call) is leveraged by an attacker. The pingback feature is exploited when multiple links can be generated from a compromised host which sends more requests for data from a WordPress server than the target can handle.
The impact to companies
DDoS attacks create more requests to a server than it can handle, thus refusing the incoming requests of legitimate traffic and customers. As websites are the common gateway to a company’s services, disrupting a web server’s capacity to handle requests can temporarily take a company offline. Where business operations might rely on consistent uptime and availability, service disruptions and outages have the potential to cause significant financial loss and may result in irreparable reputational damage. This not only affects customer trust and satisfaction, but also makes customers move away from online platforms which ultimately brings the customer base down. With a lower customer base, companies are likely to experience reduced revenue and lower conversions. This is why DDoS mitigation measures and techniques are important to consider befoe they occur.
DDoS Attack Detection
Detection of an active DDoS attack depends on the attack size, the targeted server’s capacity to handle the incoming requests, and whether or not any uptime or performance monitoring systems are already deployed to trigger alerts. The immediate impact of attacks can range from intermittent performance issues such as slow form submissions and page rendering, to issuing 503 error responses and complete server crashes.
The following server-side commands can help manually investigate and identify an attack source:
Windows:
netstat -ano
Lists all the listening ports and their connections to remote IPs.
netstat -ano | find /i /c “80”
Lists all active IP connections being made to port 80.
netstat -na 1 | find “{216.58.204.238}”
Lists all active IP connections being made to 216.58.204.238 (example IP).
Linux:
netstat -ntu | awk '{print $5}' | cut -d: -f1 | sort | uniq -c | sort -n
Lists the number of connections each IP address makes to the server.
netstat -anp | grep 'tcp|udp' | awk '{print $5}' | cut -d: -f1 | sort | uniq -c | sort -n
Lists the number of connections the IP's are making to the server using the TCP or UDP protocol.
netstat -ntu | grep ESTAB | awk '{print $5}' | cut -d: -f1 | sort | uniq -c | sort -nr
Lists only ESTABLISHED connections, and displays the number of connections for each IP address.
netstat -plan | grep :80 | awk {'print $5'} | cut -d: -f 1| sort | uniq -c| sort -nk 1
Shows a list of IP addresses and the number of connections that are connecting to port 80 on the server.
For coordinated attacks from multiple source IP addresses, it can be useful to determine whether or not the connections originate from common subnets (such as /16 or /24).
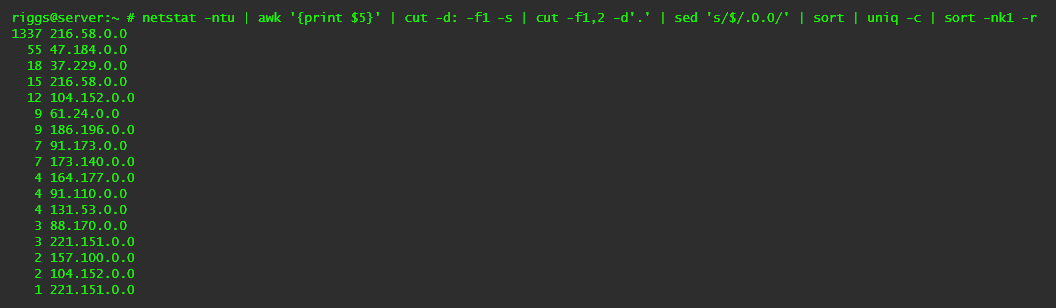
netstat -ntu | awk '{print $5}' | cut -d: -f1 -s | cut -f1,2 -d'.' | sed 's/$/.0.0/' | sort | uniq -c | sort -nk1 -r
Lists any connected IPs from the same /16 subnet which start with the same two octets (e.g. 216.58.xxx.xxx), and their number of connections.
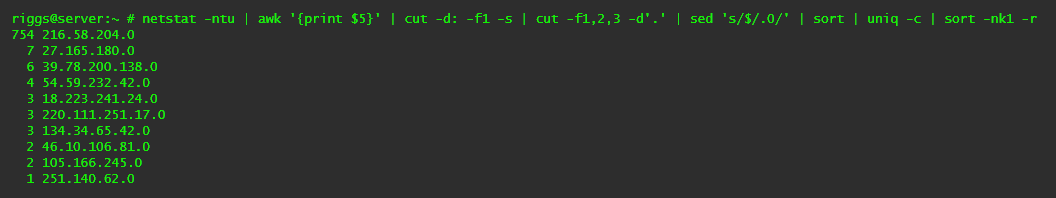
netstat -ntu | awk '{print $5}' | cut -d: -f1 -s | cut -f1,2,3 -d'.' | sed 's/$/.0/' | sort | uniq -c | sort -nk1 -r
Lists any connected IPs from the same /24 subnet which start with the same three octets (e.g. 216.58.204.xxx), and their number of connections.
DDoS Attack Mitigation
DDoS attacks require proficient knowledge and understanding of network security controls to properly mitigate. Once an attack has been detected and the abusing IP address identified, manual steps can be taken to block it.
route add 216.58.204.238 reject
Blocks 216.58.204.238 from reaching the server.
route -n | grep 216.58.204.238
A way to validate if the block was successful.
For automation, one or more of following solutions are typically deployed in hardened network infrastructure:
- Intelligent DDoS mitigation solutions – these are full-fledged systems which deflect and absorb large DDoS attack requests. The providers of such solutions provide load balancing with a scalable distributed architecture and allow for assets to be served through a CDN.
- Blocking bad traffic – protocol attacks can be mitigated by blocking bad traffic and allowing only legitimate traffic from authorised hosts. These solutions rely on a system which determines from request characteristics whether or not specific requests to a server are legitimate (through a human) or an attack (through a bot or automated).
- Absorbing based mitigation –a global network of scrubbing centers that scale, as needed and on demand, to absorb large-scale DDoS attacks.
- DDoS protection for IPs – this mitigation technique includes protection for L7 attacks that target particular websites or services hosted in the cloud. This is now mostly adopted by companies who opt to use cloud-based infrastructure.
- DDoS protection for websites – this approach detects malicious requests to web servers and protects websites against L7 attacks that target web applications. It is achieved by deploying a cloud-based web application firewall (WAF) to block malicious bots and requests.
- DDoS protection for networks – this type of solution protects networks with high-packet processing capabilities which mitigate some of the largest DDoS attacks. The various deployment models used to achieve this mitigation technique include GRE tunnels, Equinix Cloud Exchange, and Cross Connect. A flow-based monitoring approach is also deployed where needed along with support for automatic switch-over.
Top DDoS Mitigation Solution Providers
There are a number of third-party providers on the market offering high-capacity on-demand DDoS attack prevention, detection, and mitigation services. Below are some of the top providers I would recommend.
| |  Akamai Akamai | |
|---|
ABOUT THE AUTHOR

